Hello Everyone !
Welcome to the first article of Juice Shop series! This web application is coded with JavaScript, which has been deliberately left vulnerable. In this series, we’ll see OWASP Top 10 and other critical vulnerabilities.
Juice Shop has multiple installations. My advice to you should set it up at Local. Because some tasks are not active which they are website(herokuapp) and Docker.
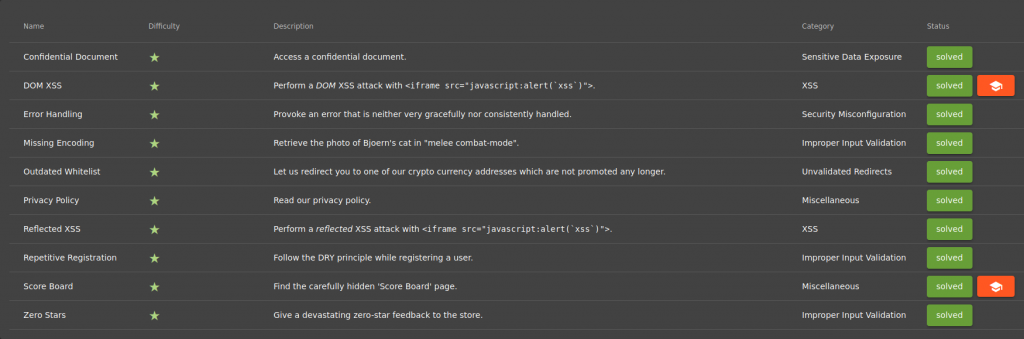
It consists of 6 Levels, 90 Missions in total. At Level 1, we’ll practice through these categories;
- Sensitive Data Exposure
- XSS
- Security Misconfiguration
- Improper Input Validation
- Unvalidated Redirects
Let’s start !
I think our first priority should be understanding the website. I mean, what does this website do? Is there a membership system? What programming language is it written in? etc. Finding answers to such questions will take us one or two steps ahead. When we first enter our website, we encounter the following tips respectively;
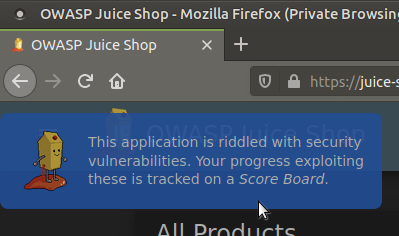
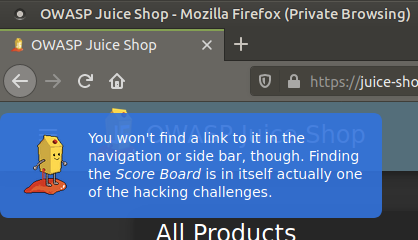
As a clue, we will find vulnerabilities in the web application by looking at the tasks in the “Score Board” section. Since this section is not in Navigation and Side Bar, we will use our internet browser’s Developer Tools. These tools have a wide range of functions, from examining the HTML, CSS, and JavaScript codes of the installed page to the assets the page wants and how long it takes to load those assets. I’ll be using Firefox. Shortcut key is F12…
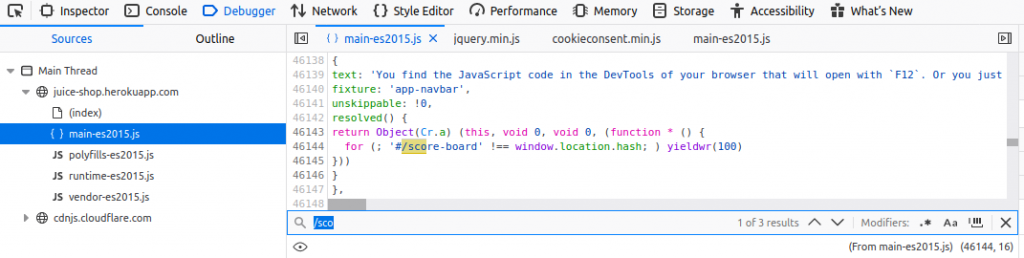
Debugger allows you to track or change the status of JavaScript code step by step to help you track errors. After clicking on the Debugger tab, I inspect “main-es2015.js” You can see the site’s JavaScript codes in general here. First task was to find the “Score-Board” section. I typed “/sco” into the search section and we found its routing.
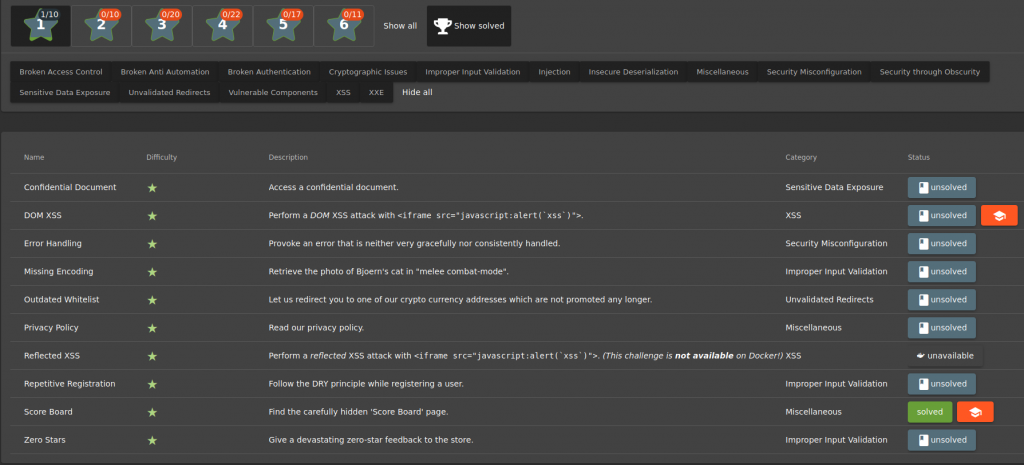
TASK – 1
Name: Confidential Document
Describe: Access a confidential document
Category: Sensitive Data Exposure
Your personal information can be exposed in different ways. Sensitive data exposure is one way. A data breach is another.
Our first task is to access a confidential document within the site. Here you can use the Burp Suite tool. When you start surfing through the browser, Burp will map the sites you’ve visited for you. As you browse, Burp Suite will add the links it has discovered to the Site Map tab.
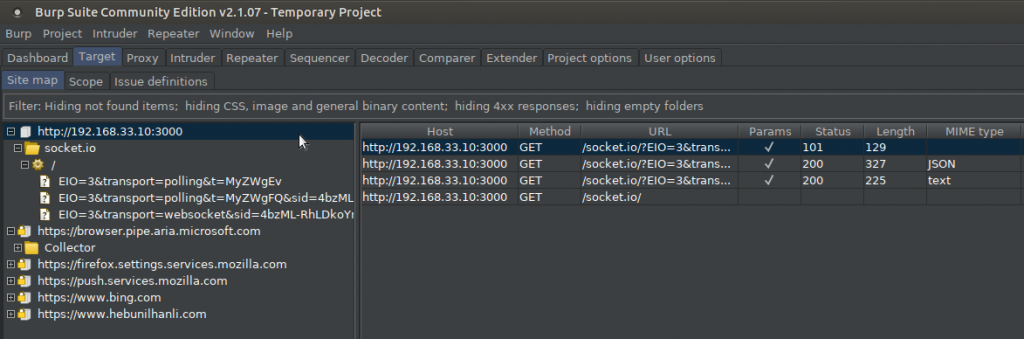
But I’m also going to use the dirb tool here. Dirb performs a Bruteforce attack and analyzes the response and scans the subdirectories in the target system.
#dirb http://localhost:3000/
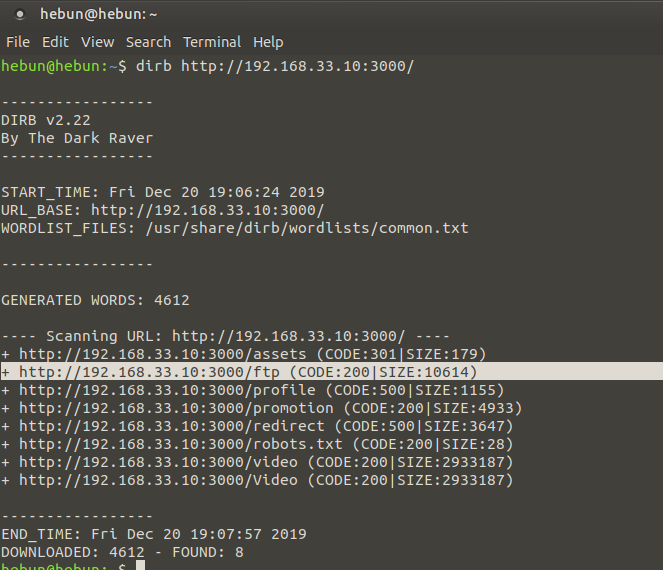
Let’s look at indexes with HTTP status codes of 200. It means that the request is successful.
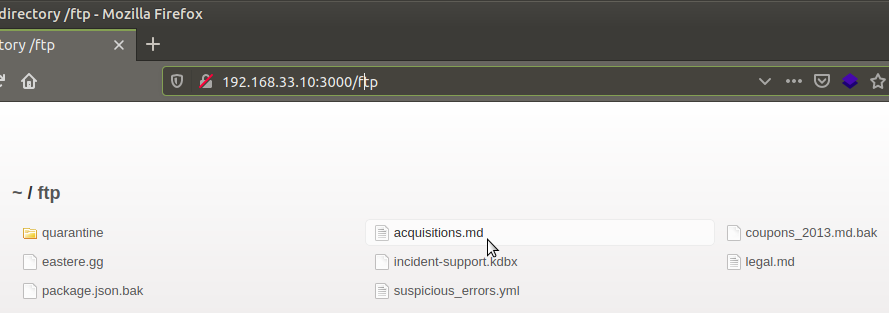
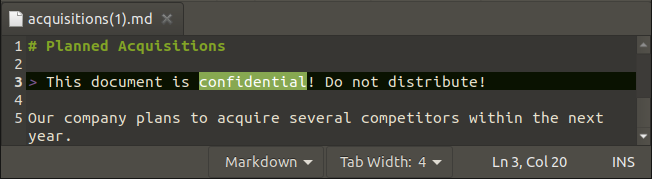
When we examined the “acquisitions.md” file inside the FTP directory, the file was warned about the confidentiality of the document. When we check the score-board again, we see that we’ve completed the mission.
TASK – 2
Name: DOM XSS
Describe: Perform a DOM XSS attack with "<iframe src = "javascript:alert('xss')">".
Category: XSS
Second task is to identify DOM XSS vulnerability using the script given above. DOM (Document Object Model) is an interface in which the HTML file can be displayed as an object and associated with JavaScript. For example, tags such as ,<head>,<body>,<img>,<h1> on the HTML page
are DOM objects.
When we say DOM Based XSS, what we need to understand is the XSS vulnerability that comes with DOM. Stored and Reflected XSS attacks, while it is possible to see the XSS attack on the rotating page after the attack; In DOM-based XSS attacks, the HTML source and the returning response will be exactly the same. In other words, the XSS attack cannot be found on the rotating page and can only be observed during runtime or when examining the DOM of the page.
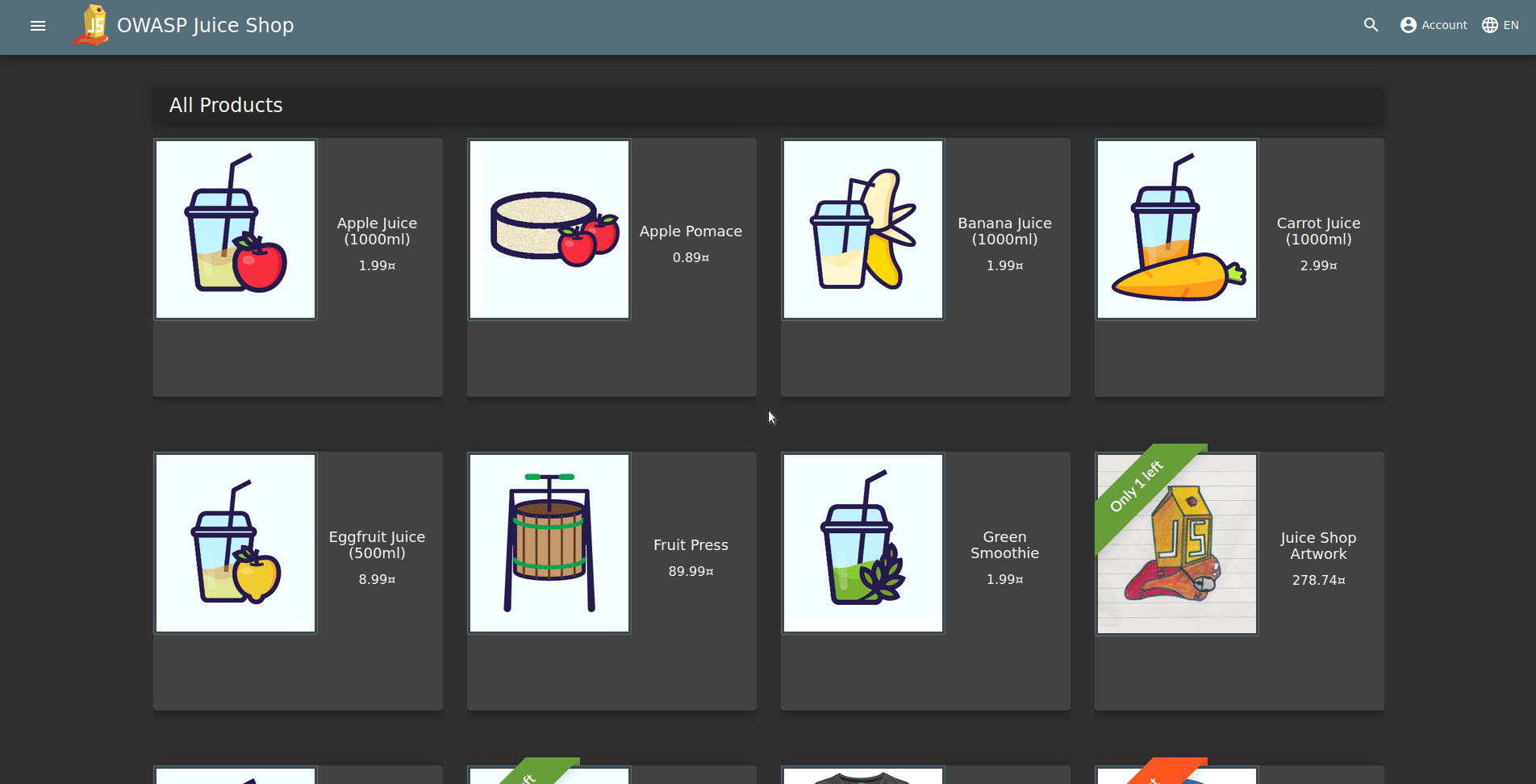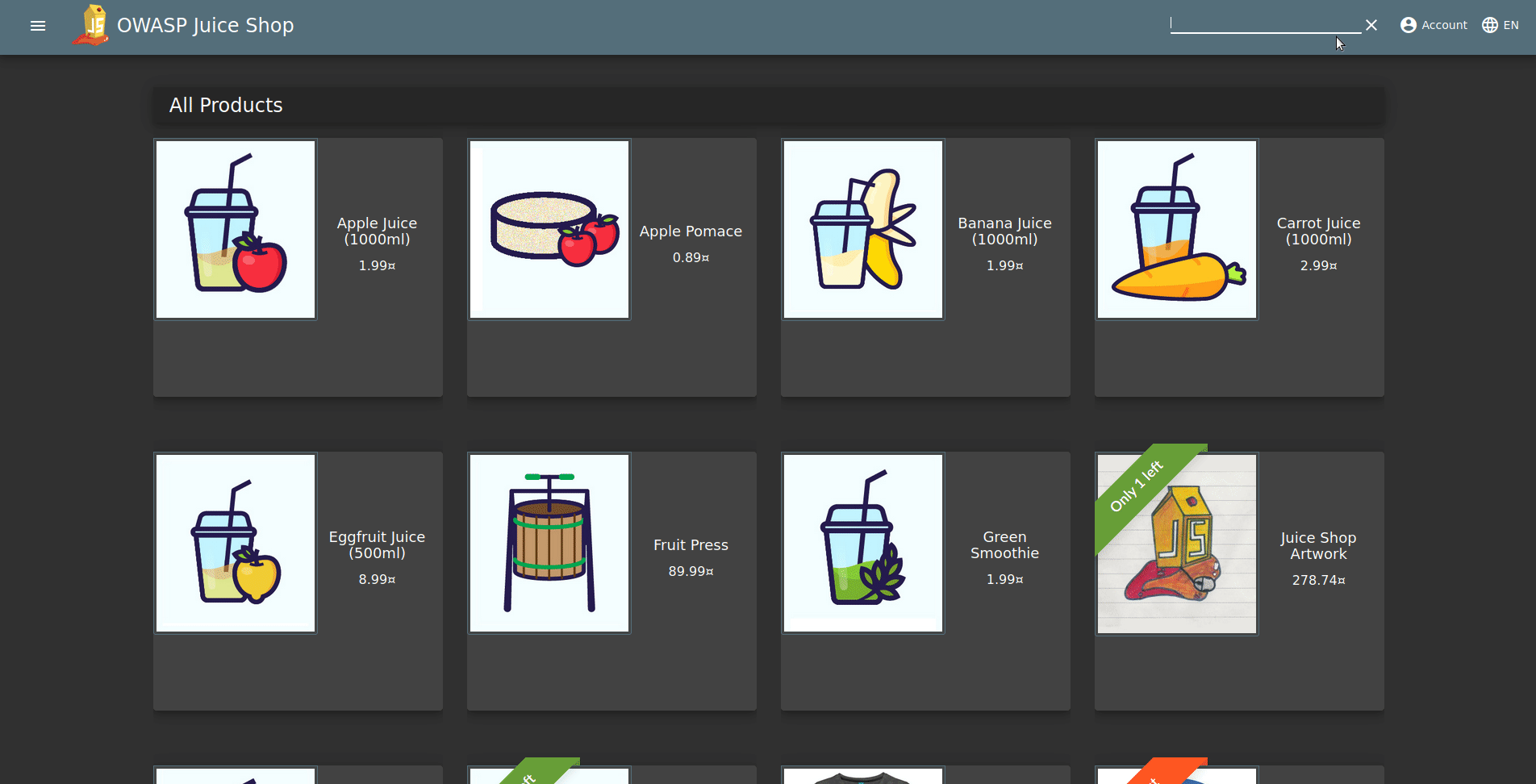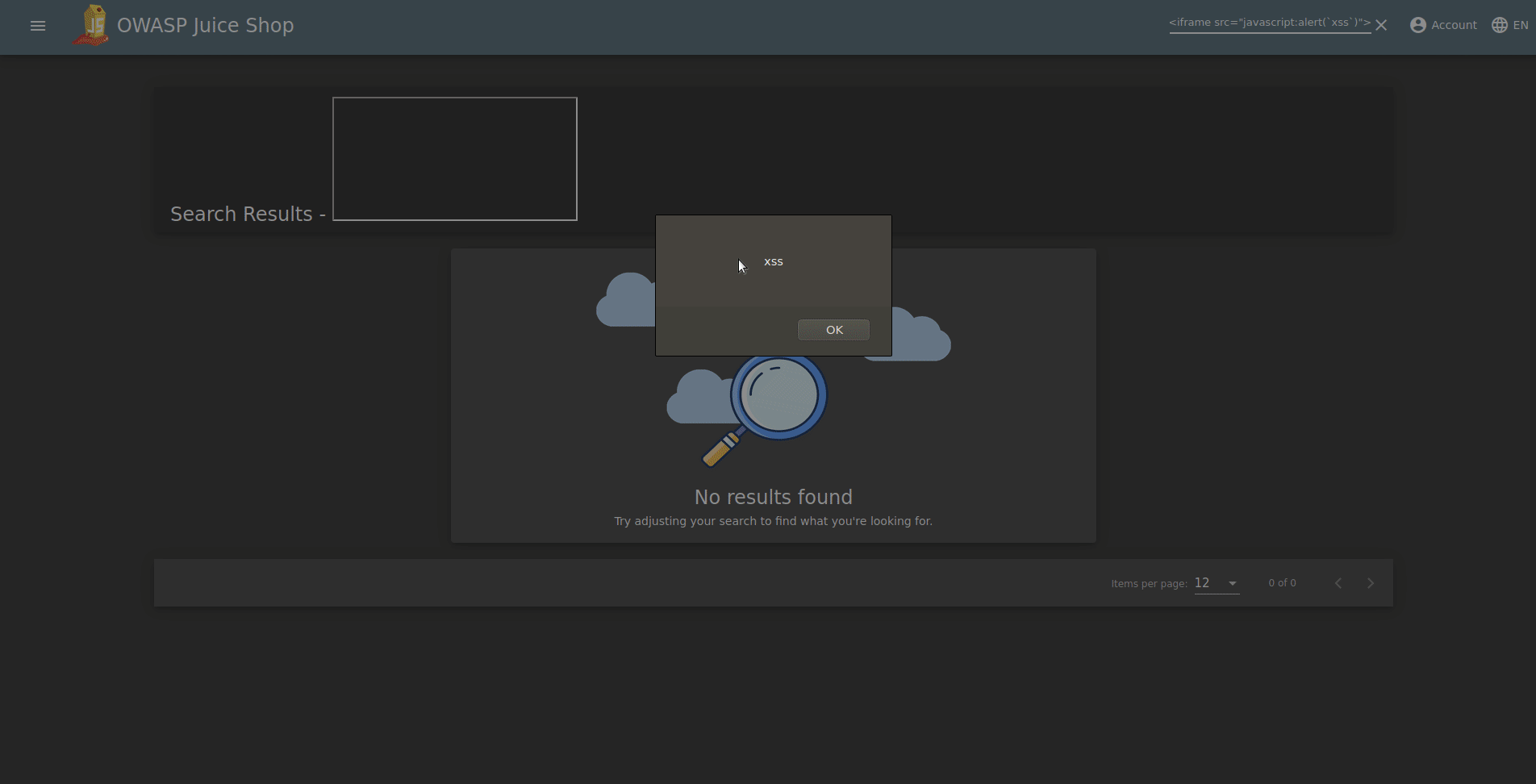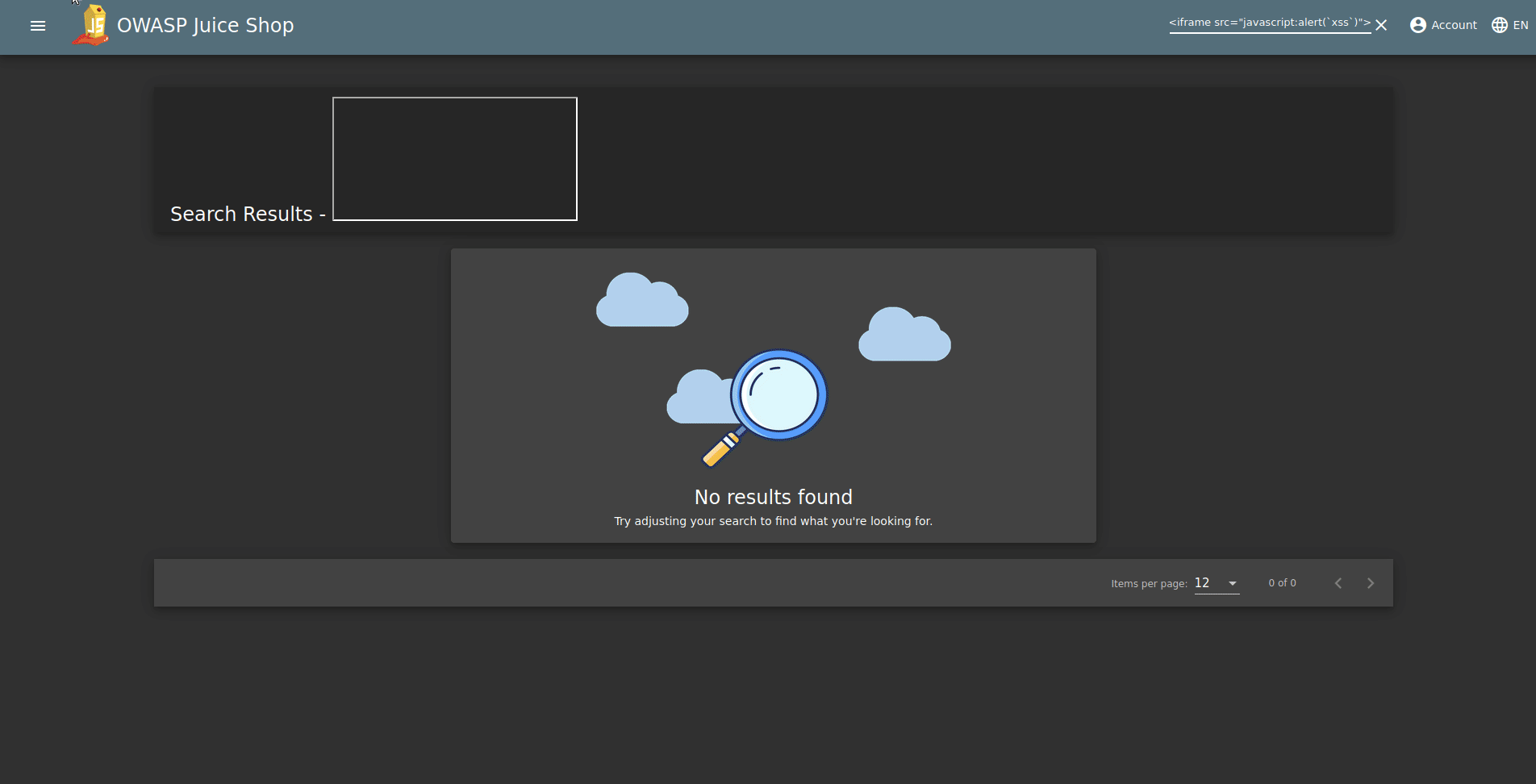
We complete the DOM XSS task when we enter our script in the search section. So how did we know that this type of attack was DOM XSS?
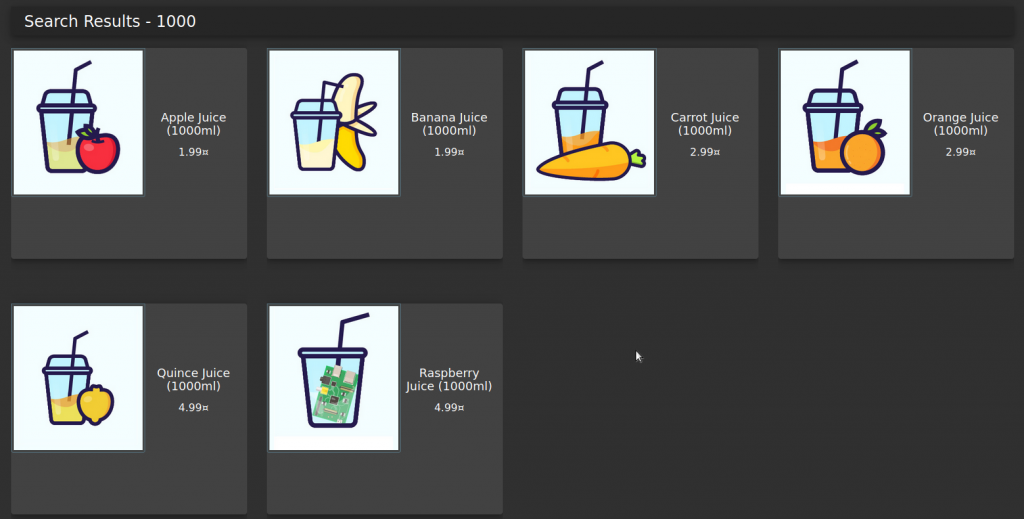
When I type 1,000 in the search section, it shows 1,000 ml of products on <mat-card>. When we check this request via Burp;
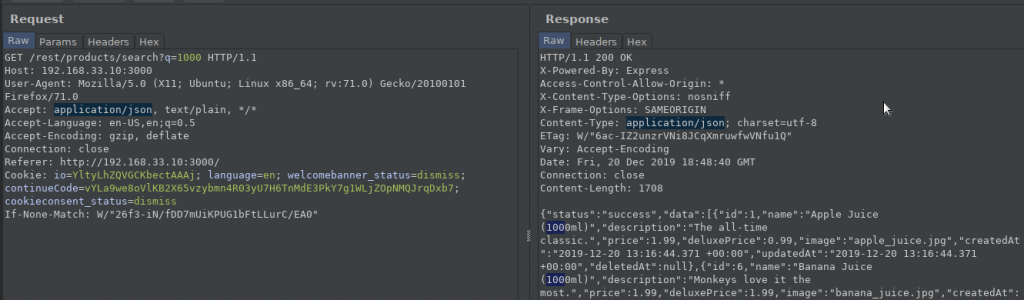
Here’s what we can conclude: “search?q=” interprets the json output it receives, creating DOMs. We find XSS because it uses the data it receives when creating DOM and sends an HTML code that the browser will interpret on the search page. Don’t forget, Because of “Creating DOM”…
TASK – 3
Name: Error Handling
Describe: Provoke an error that is neither very gracefully nor consistently handled.
Category: Security Misconfiguration
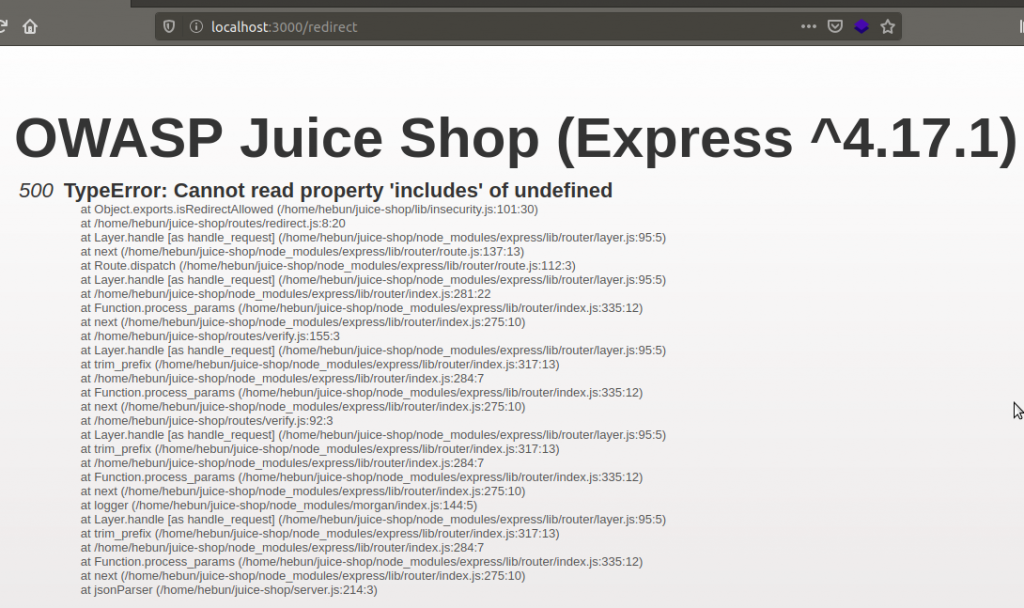
When I try “redirect” from indexes in the Figure – 6, I’m getting 500 TypeError errors.
The resulting error showed the directory of the website files which I set up at local.
Any request that cannot be properly handled by the server will eventually be passed to a global error handling component that sends an error page to the client that includes a stack trace and other sensitive information. The restful API behaves in a similar way, passing back a JSON error object with sensitive data, such as SQL query strings.
TASK – 4
Name: Missing Encoding
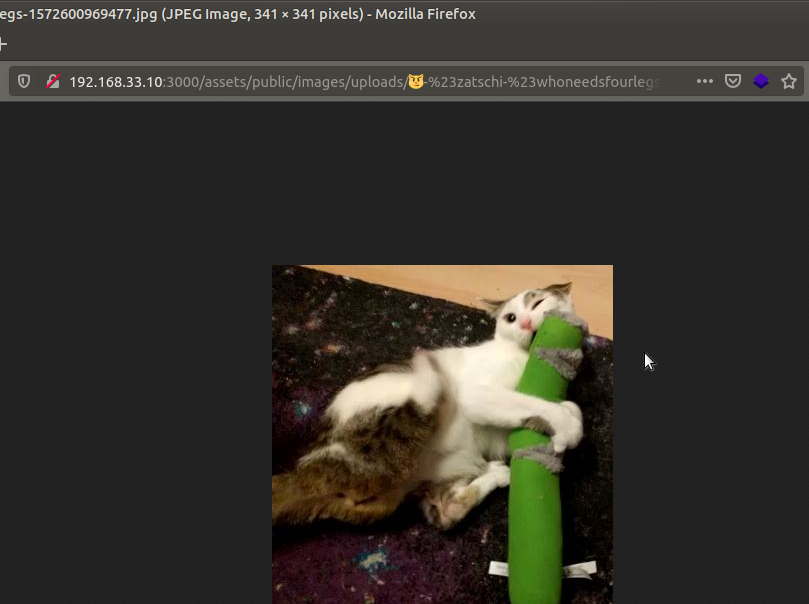
Describe: Retrieve the photo of Bjoern's cat in "melee combat-mode".
Category: Improper Input Validation
When software does not validate input properly, an attacker is able to craft the input in a form that is not expected by the rest of the application. This will lead to parts of the system receiving unintended input, which may result in altered control flow, arbitrary control of a resource, or arbitrary code execution.
Bjoern’s post does not show a picture because of the missing encode. Enter the photo wall directory by clicking on the side bar in the upper left corner.
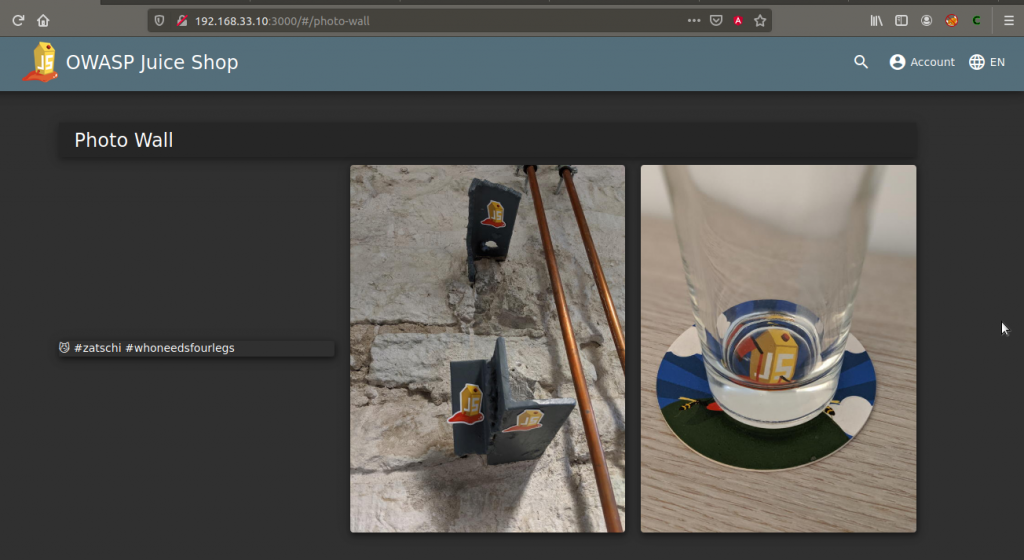
The post on the far left doesn’t show a picture. Now let’s right-click on the “😼” icon and inspect it.
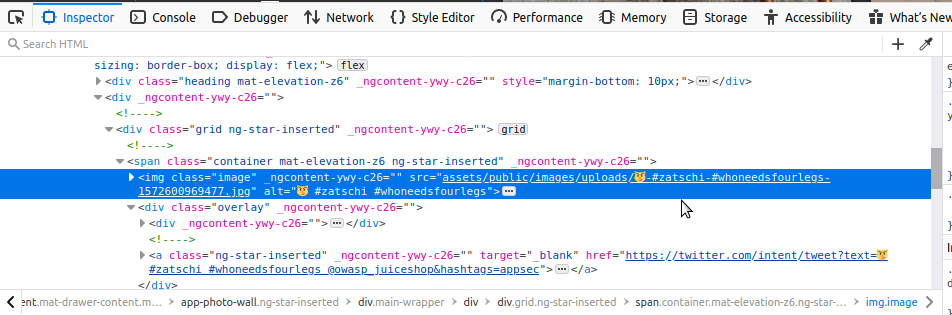
Once you know the directory with the picture, we’ll go to our address bar:
http://localhost:3000/assets/public/images/uploads/😼-#zatschi-#whoneedsfourlegs-1572600969477.jpg
You’ll notice, I deleted the phrase “#” after the port because it was written after assets “:3000/” in Figure – 6. Also, if you look at the source of the other images, it will clearly show you the directory.
Once you’ve entered the address, you’ll see a blank page. This is because the Web pages URL consists only of ASCII characters. Therefore, we will use our address to encode information that does not consist of ASCII characters in the address bar of web browsers or is likely to be confused with the address. For example, “😼” and “#” will need to be encoded because they are not ASCII characters.
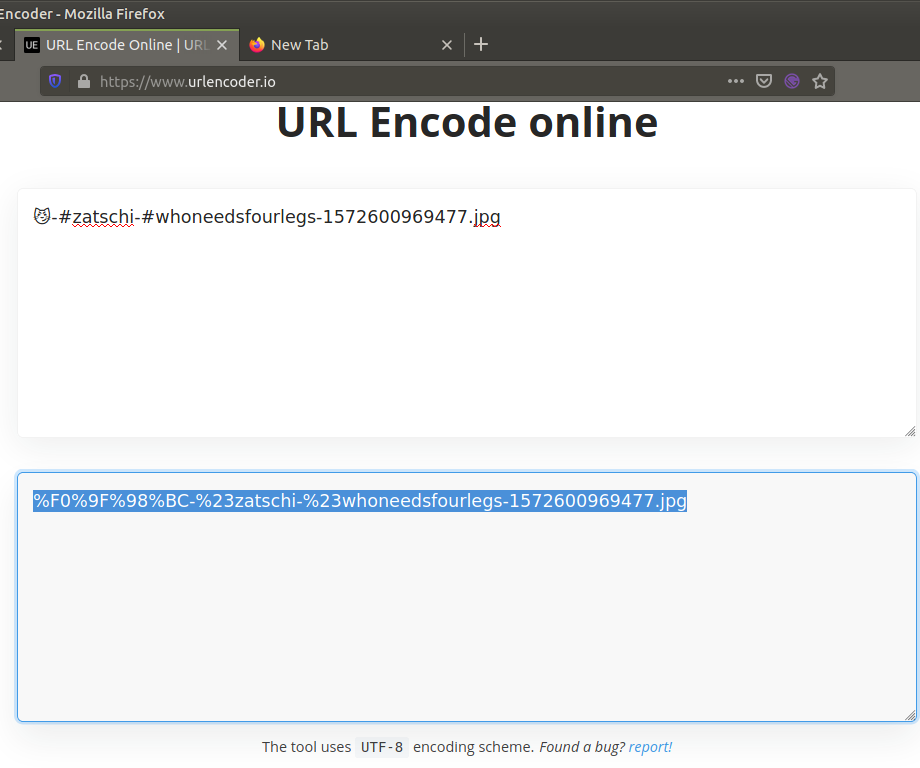
http://localhost:3000/assets/public/images/uploads/%F0%9F%98%BC-%23zatschi-%23whoneedsfourlegs-1572600969477.jpg
If the link above is entered in the address bar, the picture will be reached.
TASK – 5
Name: Outdated Whitelist
Describe: Let us redirect you to one of our crypto currency addresses which are not promoted any longer
Category: Unvalidated Redirects
Redirect, as the name suggests, performs access to a remote application. Current application parameters can be changed to direct the application to different contents.
For example, Take a company’s website. If there is a Unvalidated Redirect vulnerability, an attacker might take the opportunity to
https://example-company/redirect?to=https://<attacker-address/exploit.php
send this address to an employee’s email address at the company… The employee might click on the incoming e-mail thinking it came from the company. If we consider exploit.php’s purpose as “reverse_tcp”, after clicking, The employee’s shell opens up to the attacker and the computer is hacked. This is one of the simplest examples…
Returning to task, we are asked to find the juice-shop’s crypto currency address, which is no longer shown to the user. Access to the source code can be examined if possible, whether a “whitelist” has been created for the orientation of the existing parameters.
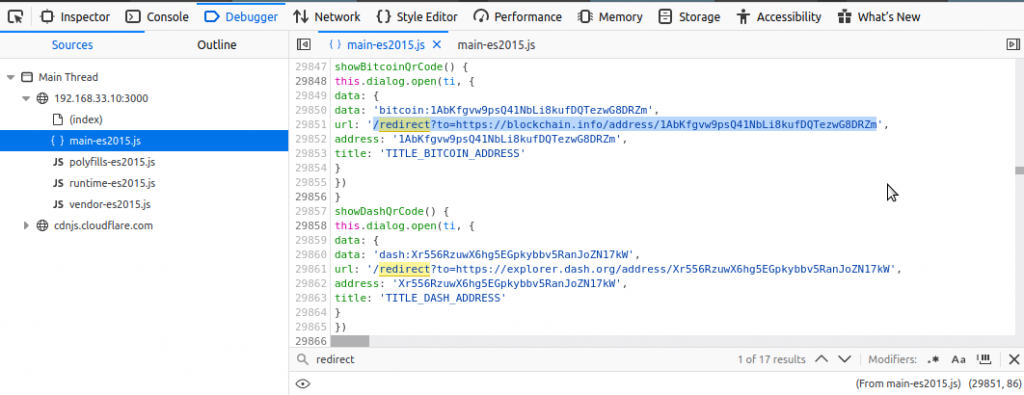
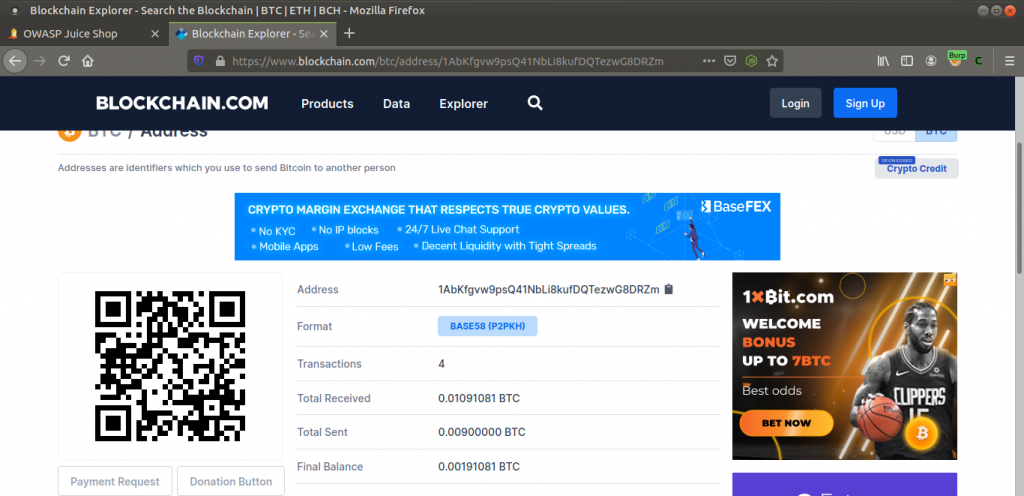
When I was reviewing the page, I typed “redirect” into the search section and identified a bitcoin address.
TASK – 6
Name: Reflected XSS
Describe: Perform a reflected XSS attack with<iframe src="javascript:alert(`xss`)">.
Category: XSS
Note: This task is only available in the local setup.
Reflected XSS attack is made to URL fields or data entry fields. This attack is only seen by the user who launched the XSS attack. Visitors can’t see this attack.
For example, in Reflected XSS attacks running on the URL, an attacker can create a script that can steal a user’s cookie and send it via email.
The primary task will be to explore the input sections on the site. You must become a member and log in to use all the functions on the site. That way we can use other input.
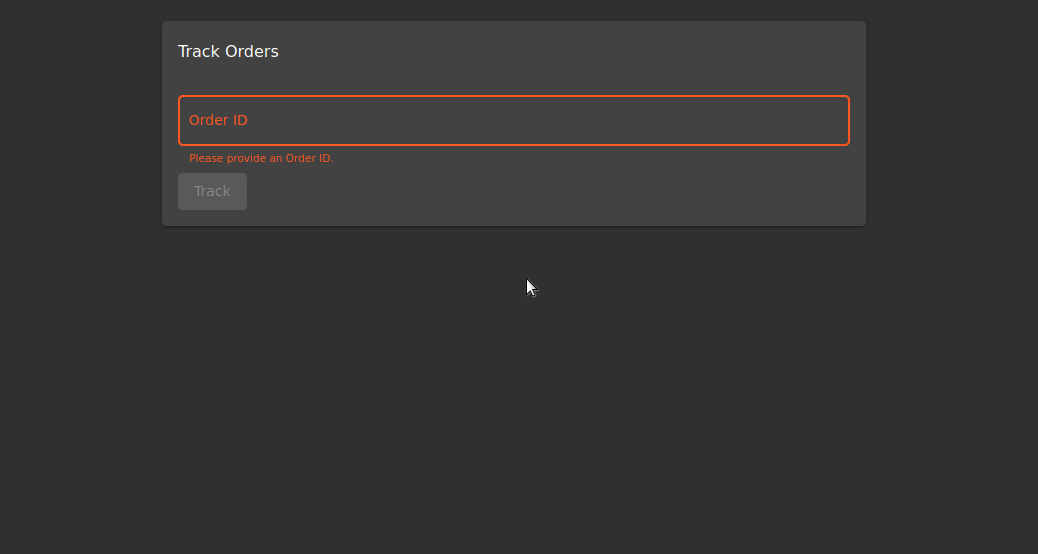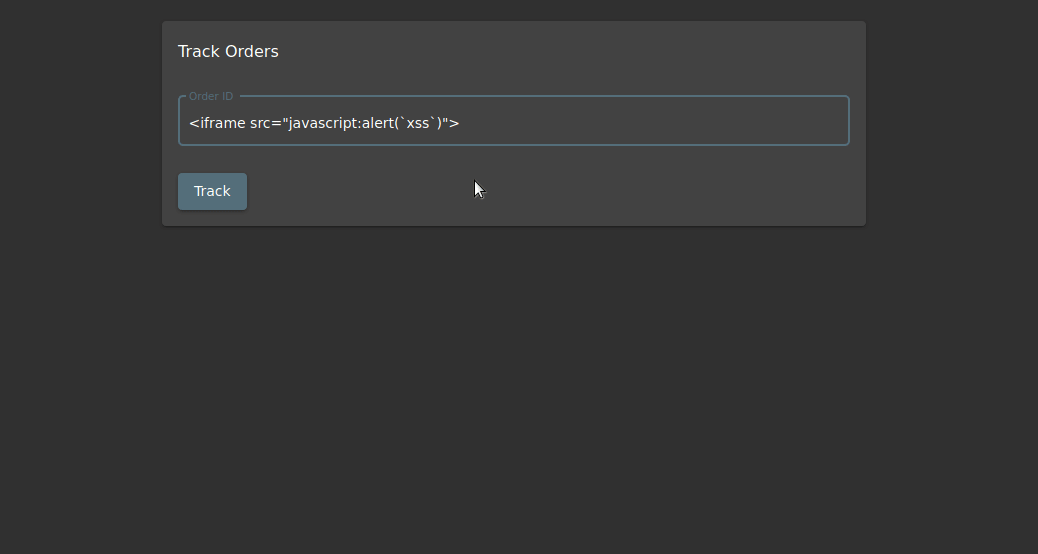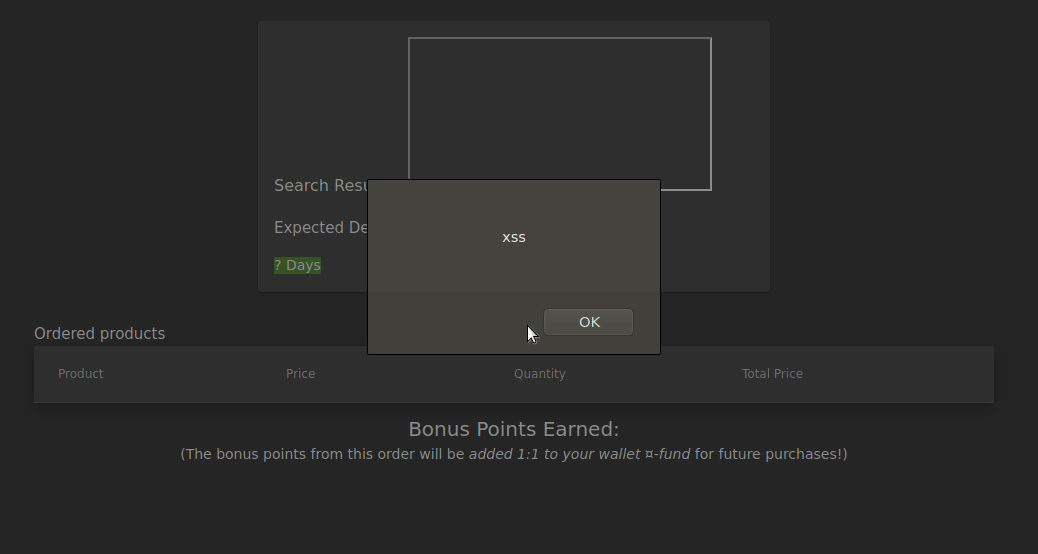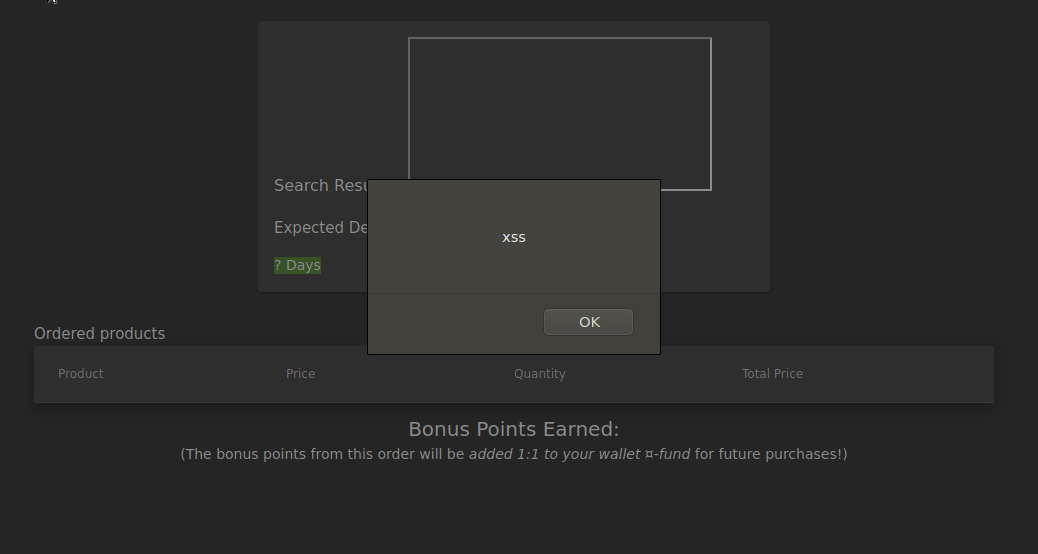
At the end of the Web Enumeration, Reflected XSS were found in the entry in the “track order” section. I want to show the difference in our previous XSS mission with BurpSuite.
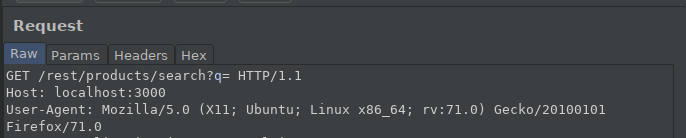
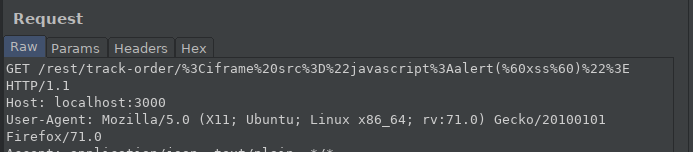
After the Reflected XSS attack, we were able to see the XSS attack on the rotating page. However, the DOM XSS attack cannot be found on the rotating page. It can only be observed during runtime or when examining DOM of the page.
TASK – 7
Name: Repetitive Registration
Describe: Follow the DRY principle while registering a user.
Category: Improrer Input Validation
According to dry principle, the programmer must avoid code repetitions during coding. Repeating the code itself (e.g. using copy-paste method) often makes it difficult to maintain and improve the software system.
In the membership section, we will identify vulnerability by taking into account the DRY principle.
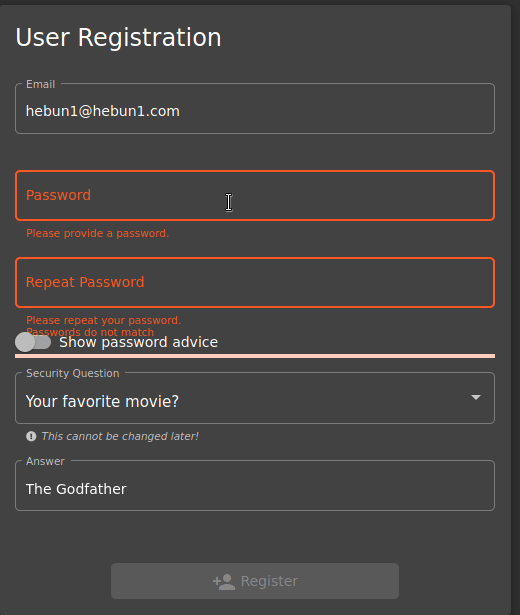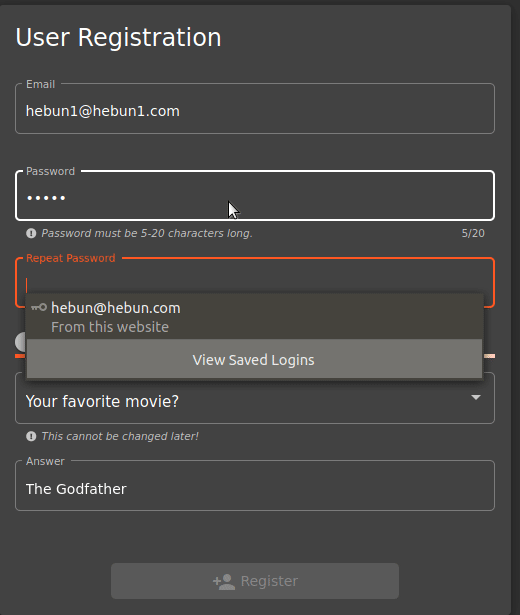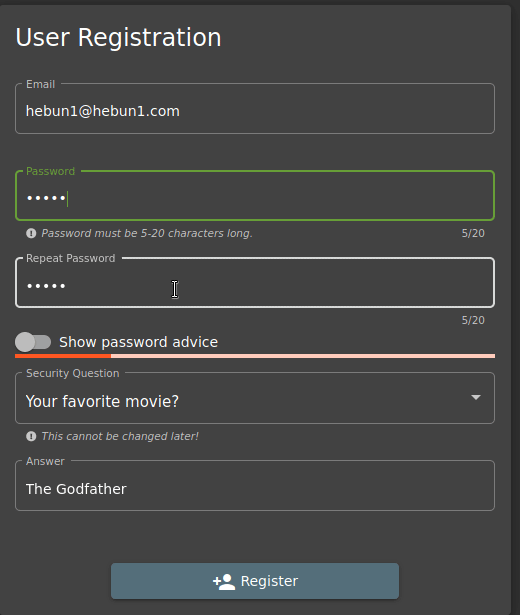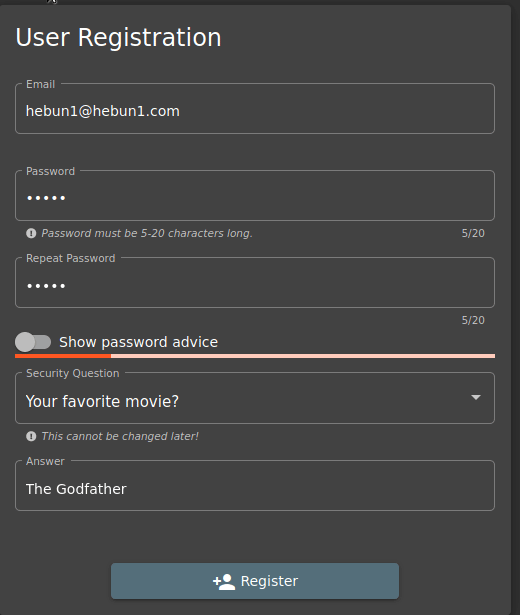
As you can see in the Figure – 21, I can’t complete the membership process when Password and Repeat Password aren’t the same. What if I changed the input order?
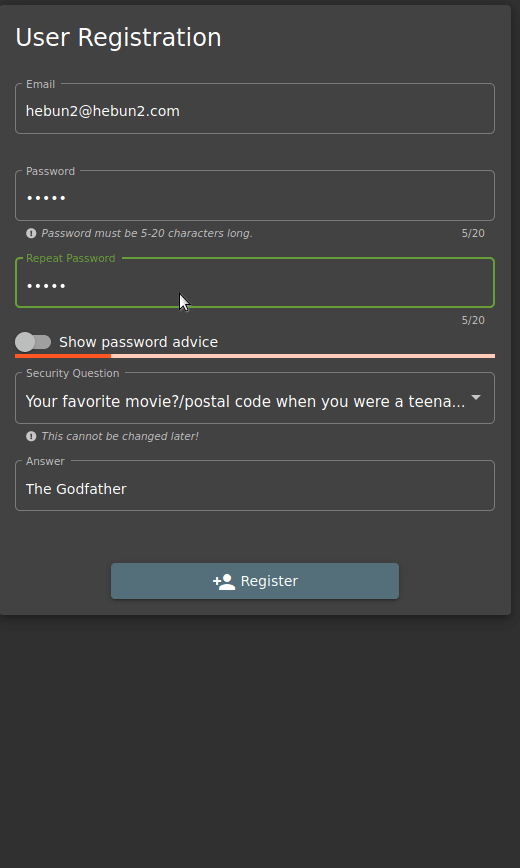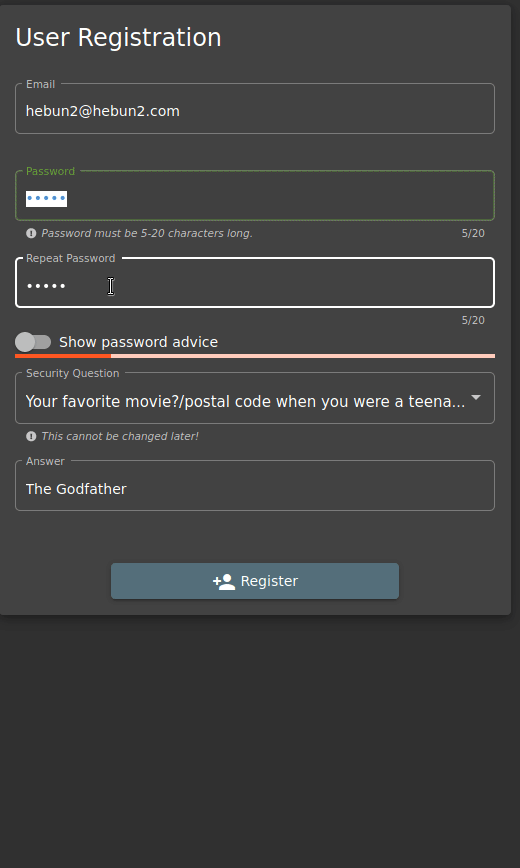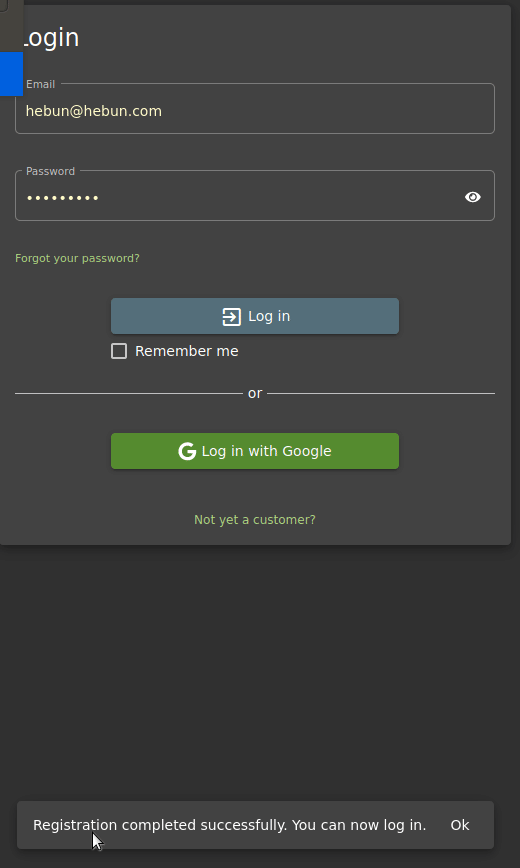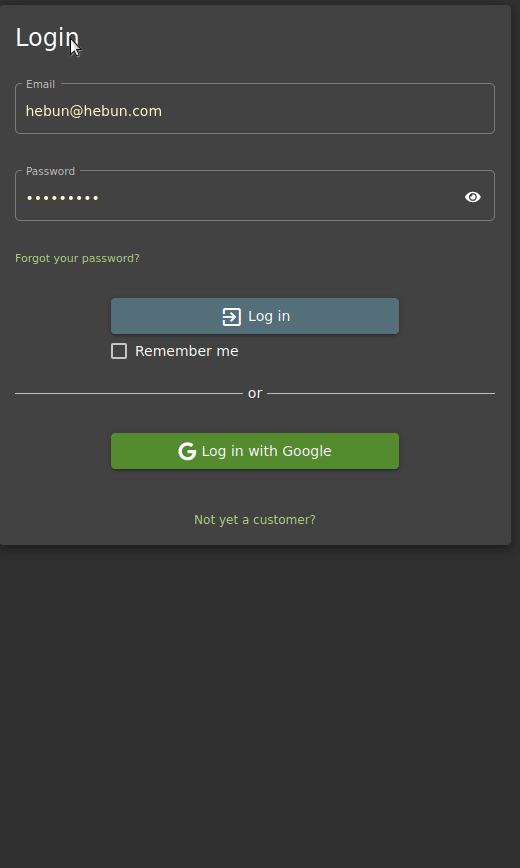
I type “12345” into Password, then I go to Repeat Password and write the same password. There are no problems… When I go back to the Password entry and change the password, the system still says the password is compatible. Here we see that the person who created the software does not comply with the DRY principle.
TASK – 8
Name: Zero Stars
Describe: Give a devastating zero-star feedback to the store.
Category: Improrer Input Validation
The last task is to send feedback to the site without giving stars in the rating section.
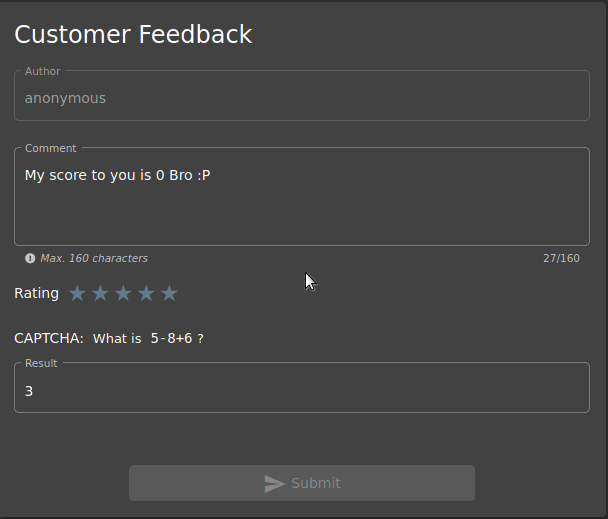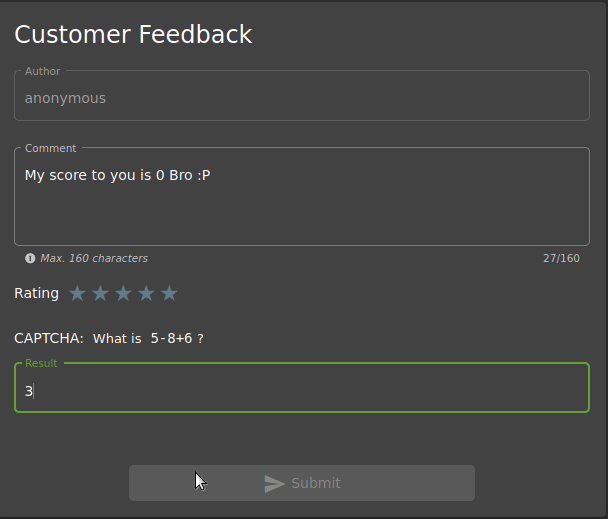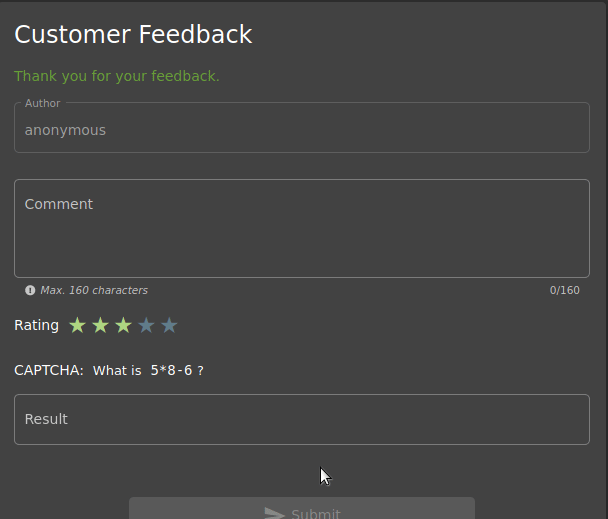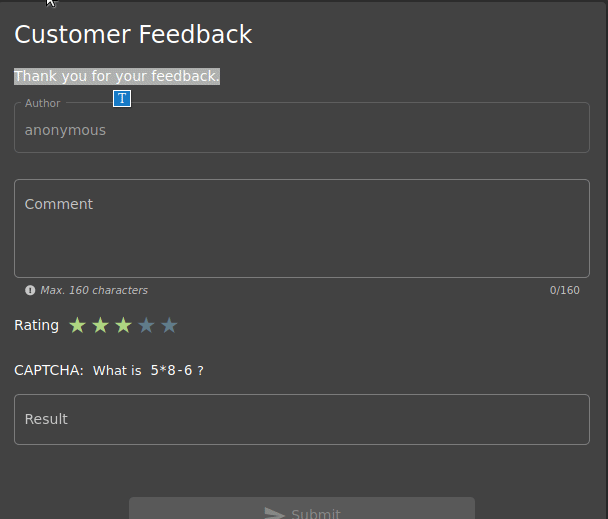
As shown, you cannot use the Submit button when the rating section is not filled. So can we activate the button from Developer Tools?
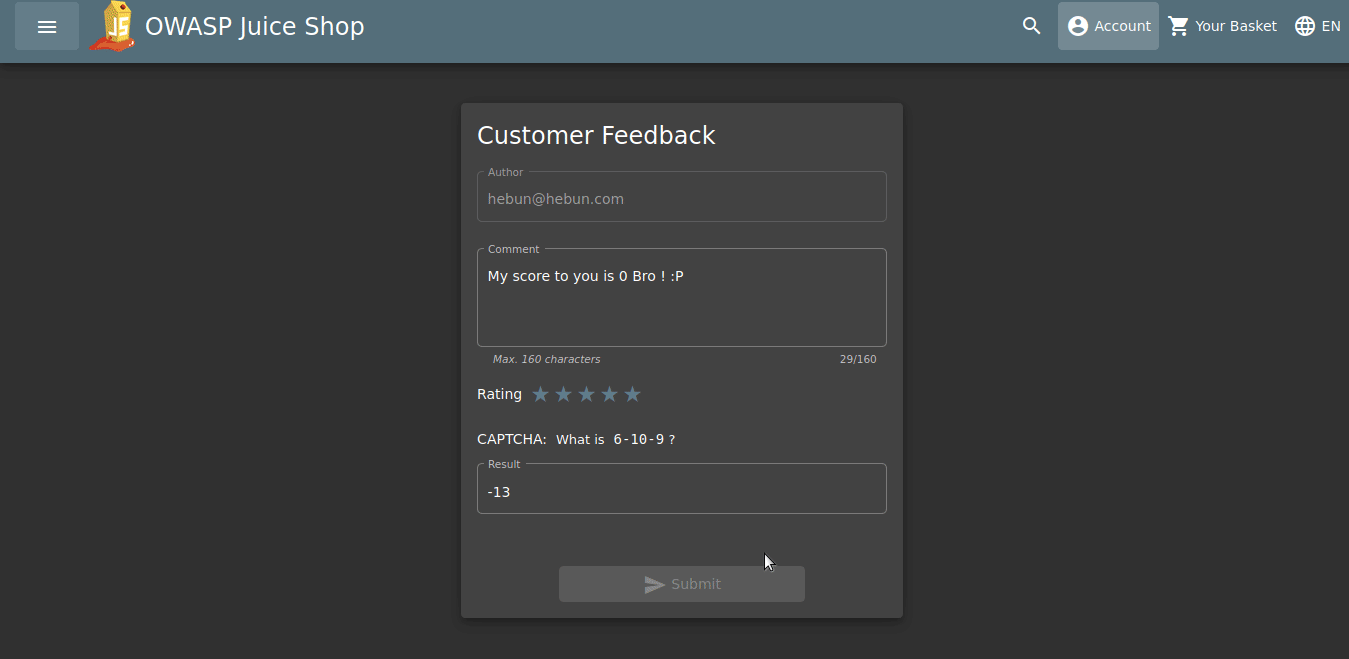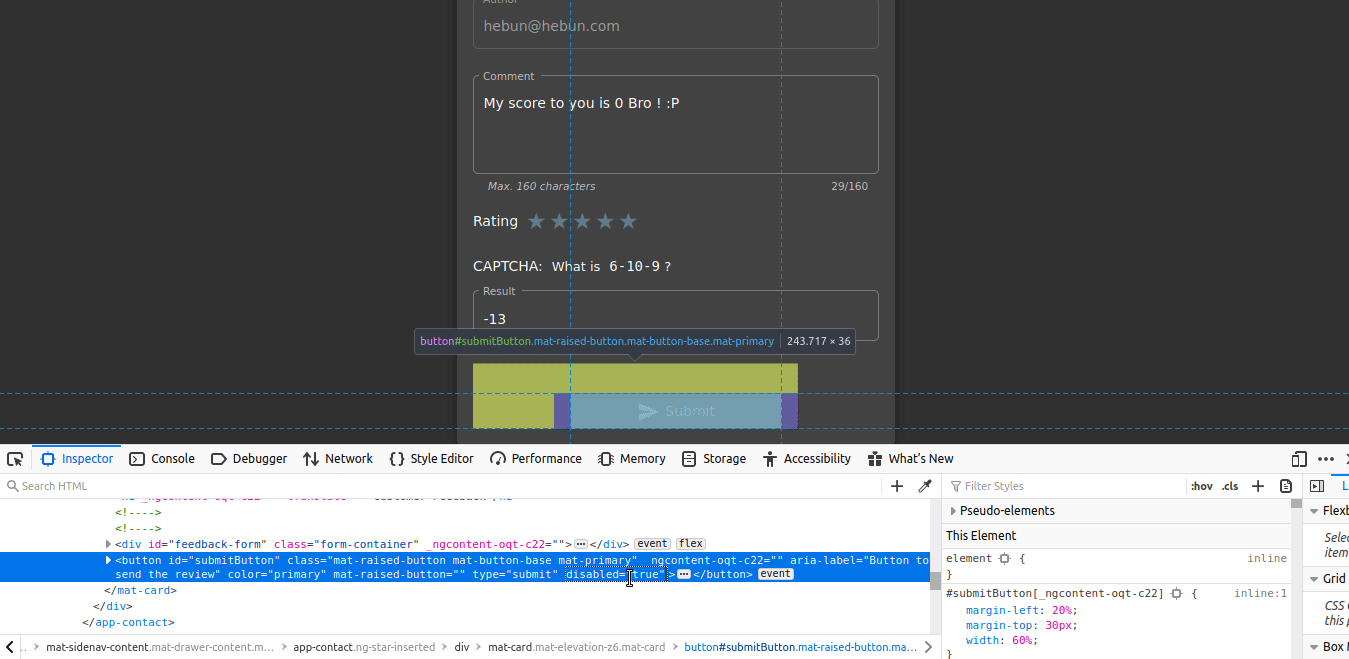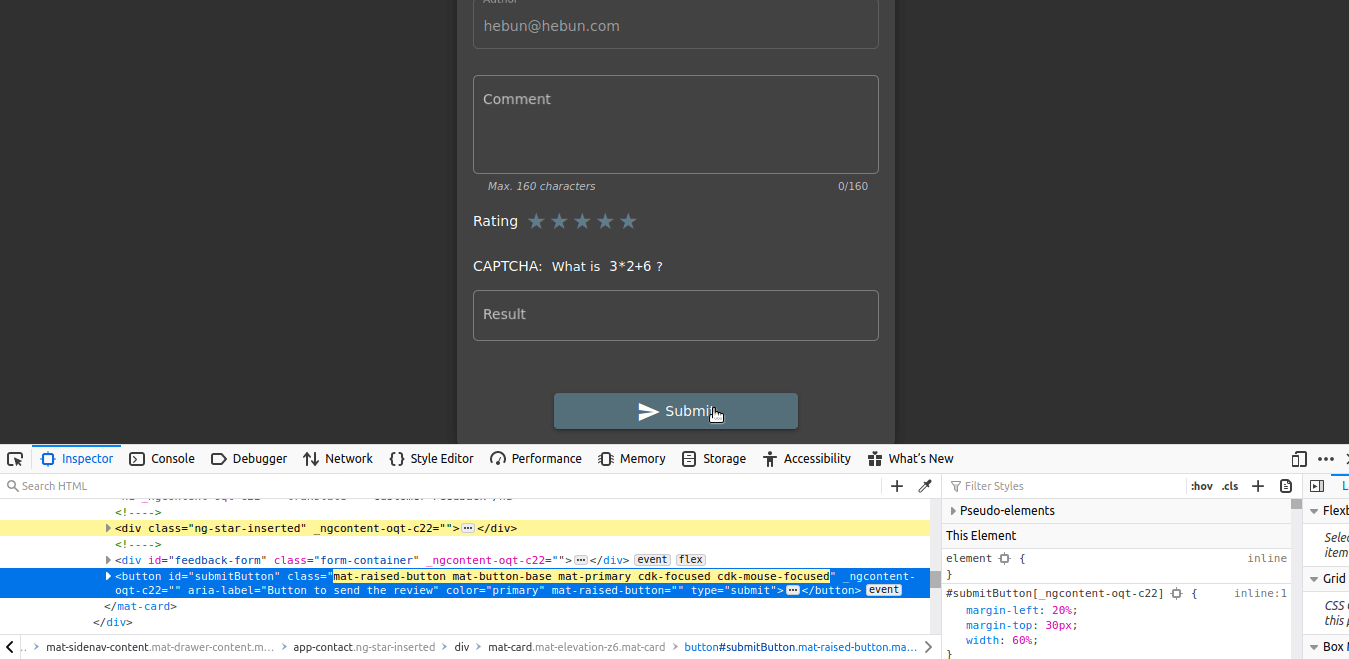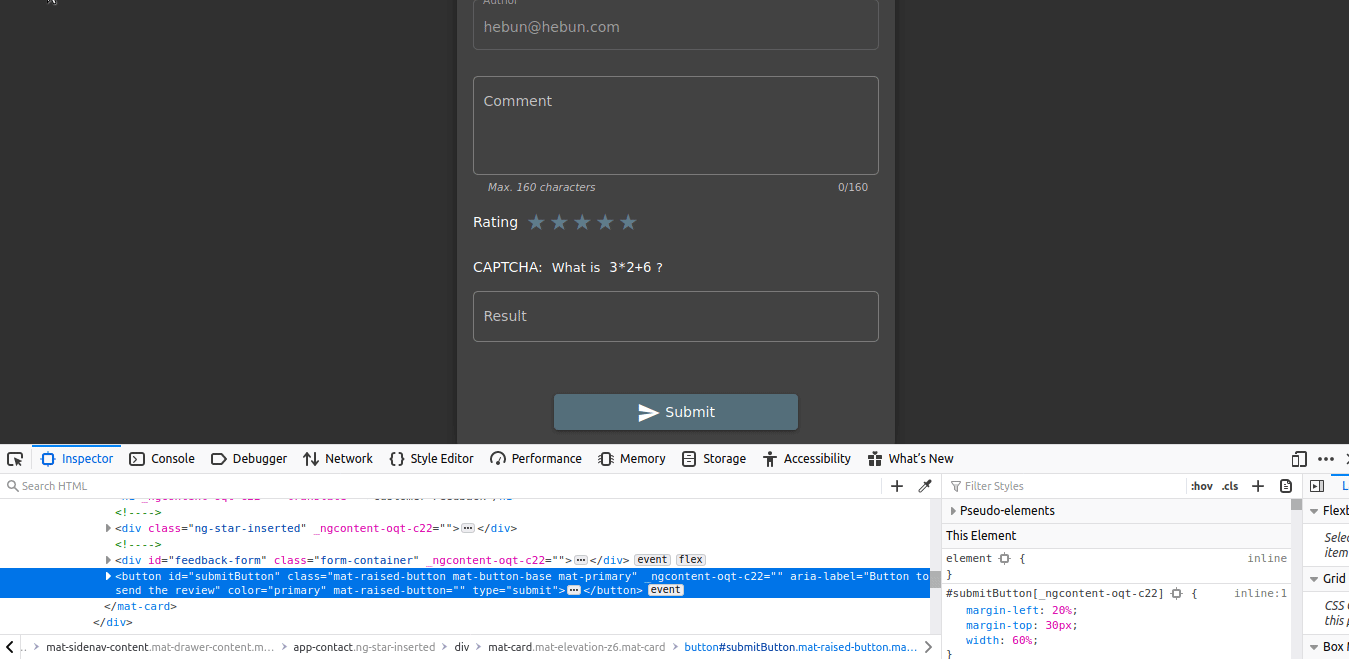
In Developer Tools, when disabled=”true” is deleted, you’ll see that the Submit button is active.
I hope I’ve used language that’s understandable enough. If I have a mistake, please contact me.
See you in the new article…


May I know how to prevent this part?
It is confirmed is on improper input validation? very hard to search similar attacks like that, I want to find the prevent to this problem.
Name: Missing Encoding
Describe: Retrieve the photo of Bjoern’s cat in “melee combat-mode”.
Category: Improper Input Validation
Hi Geean,
The reason for such errors is the incomplete or incorrect coding of the developers. Consider the entry you received from the user … If this entry does not correspond to ASCII characters, you can save this entry as URL encoded in the database. If you want to parse your application, you can present this input to the client as decode. It should be “Don’t trust the input of any user” here. Therefore, receiving special characters as encoding will prevent such vulnerabilities.