Hello Everyone !
I’d like to share with you the second article of our Juice Shop series this week. I know I haven’t shared a post in two weeks… From Mustafa Akgül Özgür Yazılım Winter Camp, I was unable to share a post because I was studying Web Security and Analysis for 4 days. Now I’m with you…
At Level 2, we will proceed through the following topics;
- Broken Access Control
- XSS
- Security Misconfiguration
- SQL Injection
- Sensitive Data Exposure
- Broken Authentication
- Cryptograpgic Issues
Let’s Start !
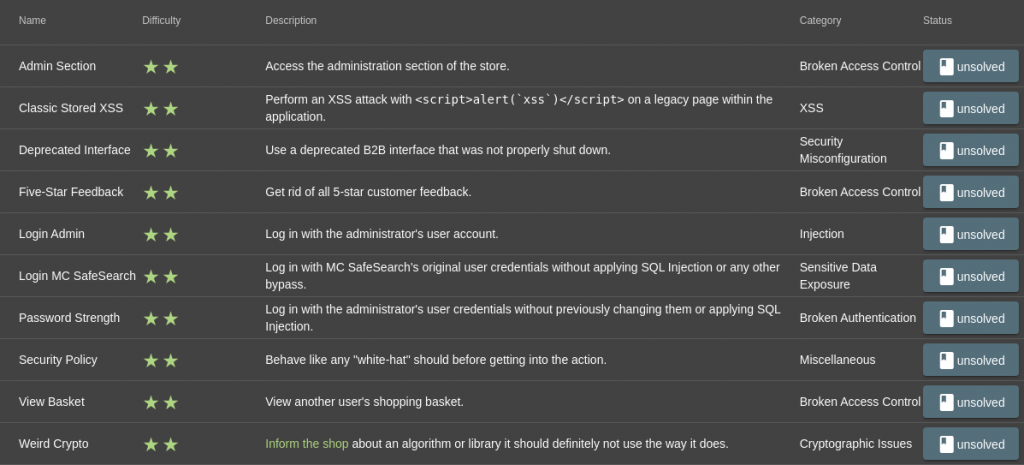
TASK – 1
Name: Login Admin
Describe: Log in with the administrator's user account.
Category: SQL Injection
SQL Injection is an attack technique used to attack database-based applications. The intent of the attack is to interfere with the query. When If there is a vulnerability in the query function, a malicious person can send unwanted queries and take advantage of it to make any changes to the database.

We need to log in with the administrator user to complete our first mission. We have to use a SQL Injection attack because we don’t know the administrator’s email address. So how ?
If I enter the “test@test.com” value in the email section, it will be functionally processed by a server-side query, and will probably be put into this process;
SELECT * FROM Users WHERE email = ‘test@test.com’
The input will be in the quotes because we need to enter a string value in the email entry. I can give you an example to better understand;

As you can see, in mysql, the SELECT command is similar to the print style in the programming language…
Now let’s go back to our mission. We don’t currently know the administrator’s email address. Then let’s send null value…
SELECT * FROM Users WHERE email=’ ‘
Of course, this query will tell us that we have entered incorrectly. And what if I get the right input in SQL ?

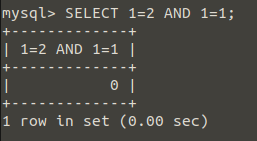
Perhaps you have studied “Mathematical logic” in your high school or university education… Logic is discipline that examines the structure of knowledge, distinguishes between right and wrong, and is the instrument of the right thought.
- In Figure – 4, 1=1 projected the proposal to output 1. That means this proposal is correct.
- But when I say 1=2, the value of 0 turns, so it seems that the proposal is wrong.
So when I log into the Juice Shop, I need to enter the values that are right, which is registered in the database. If I get in the wrong way, the system won’t accept me and I won’t be able to log in.
Let’s think of it this way;
1=2 means the e-mail that I want to log in to… 1=1 is an additional suggestion for the inquiry. What’s the result?
The answer is 0 from 0 AND 1 . Because mail is wrong…

Well, if I do the procedure as follows…
- 1=2 ——-> 0
- 1=1 ——-> 1
It’s going to be value 1 from 0 OR 1, so it’s true. I mean, if I add an additional correct suggestion to the server-side query, the process will be considered correct. Let’s test it now !
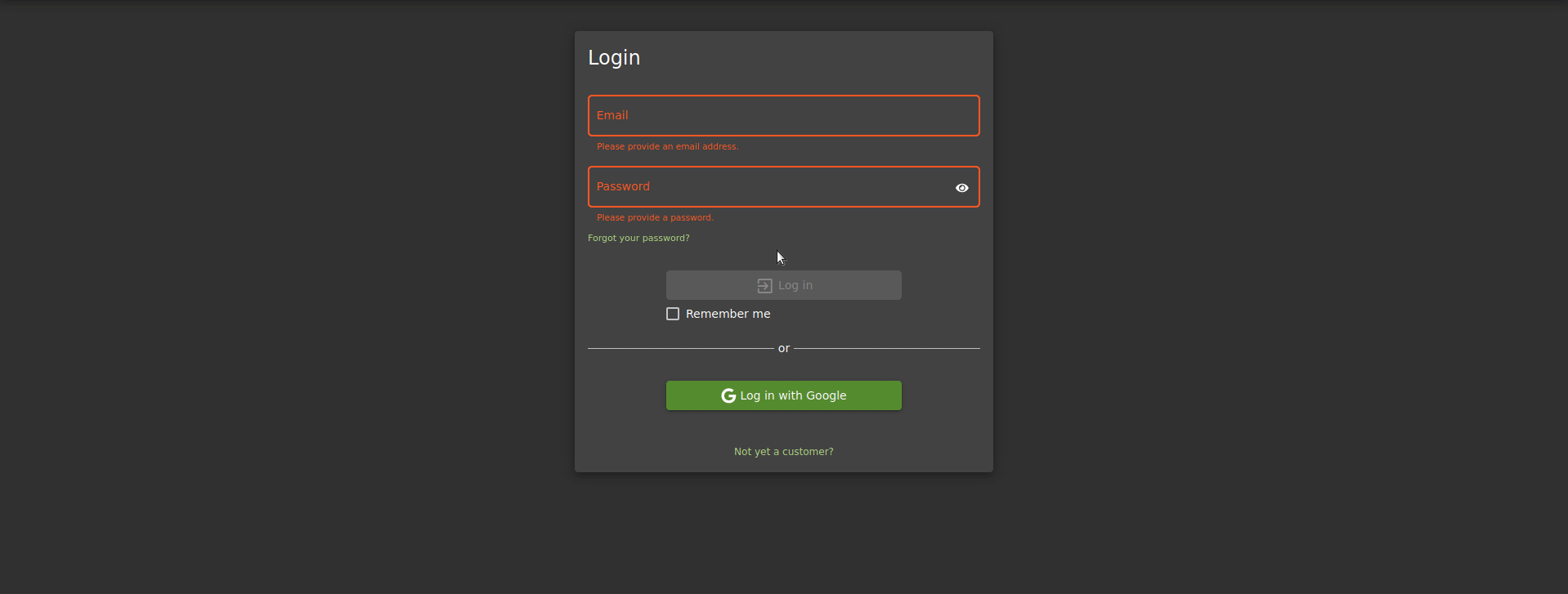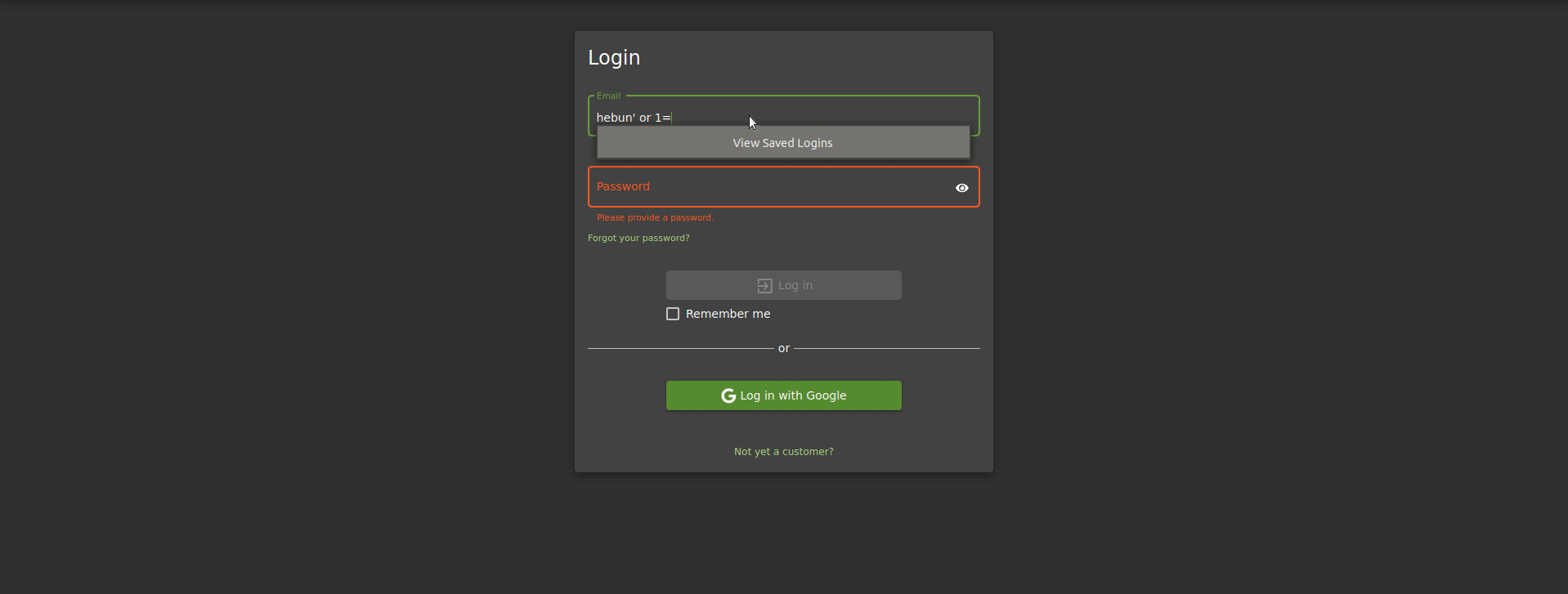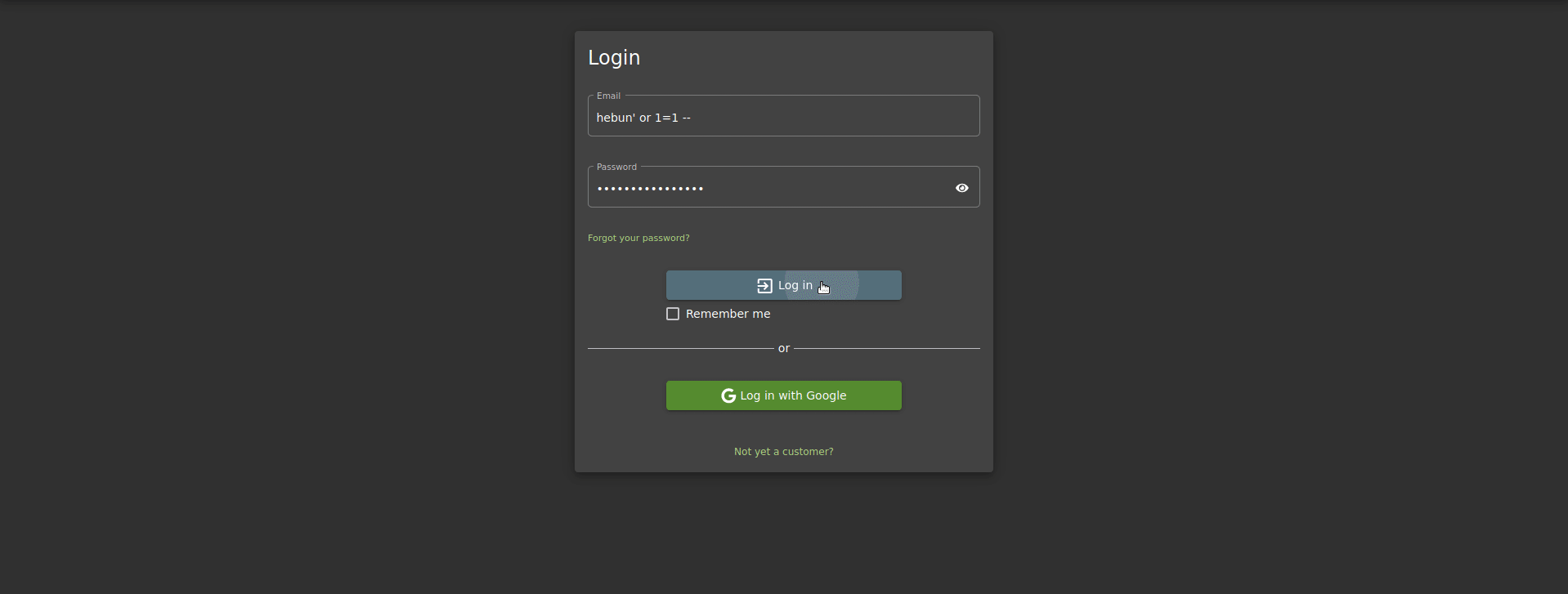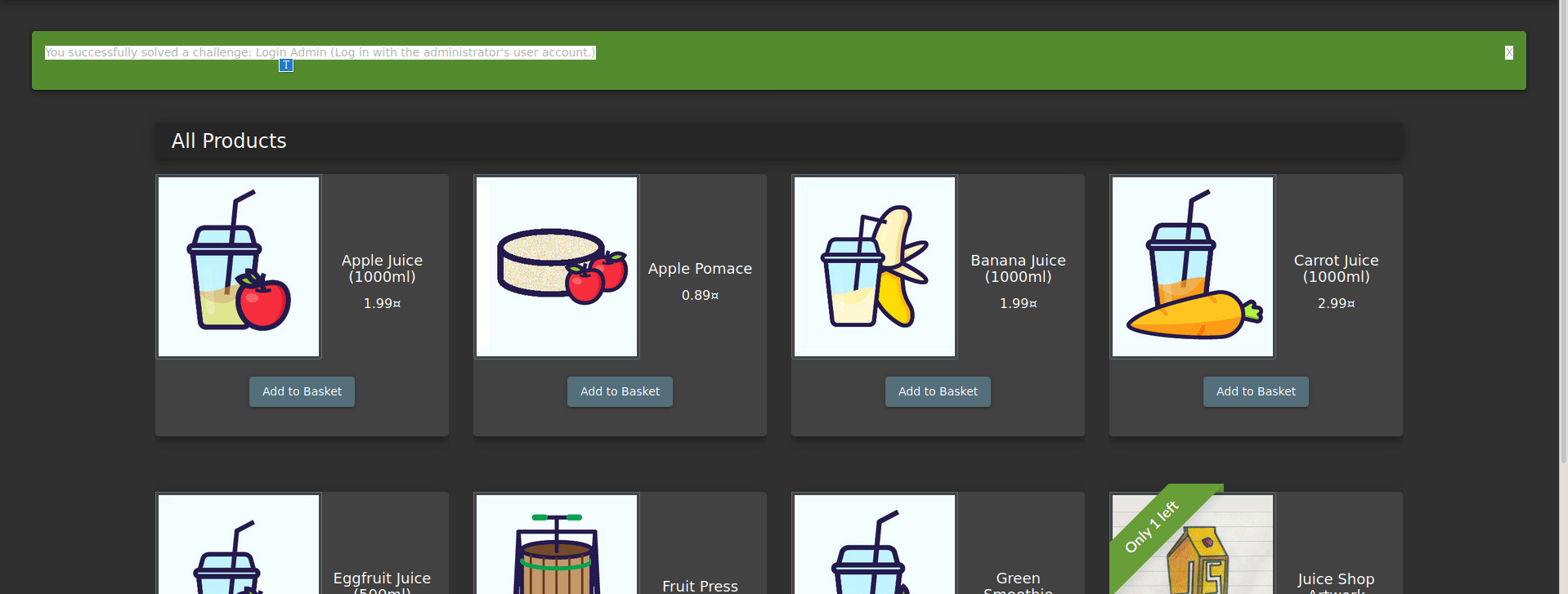
Here’s how the query happened;
SELECT * FROM Users WHERE email = ‘hebun’ or 1=1 — ‘
The reason I put “–” means a line of comments at Oracle. If you remember, the string value we sent at the beginning of the article was written in quotes. Thanks to the comment line at the end, we made it dysfunctional.
NOTE: We probably accessed that user after SQL Injection because it was probably the administration at the top of the users table.
TASK – 2
Name: Admin Section
Describe: Access the administration section of the store.
Category: Broken Access Control
Access control enforces policy such that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification or destruction of all data, or performing a business function outside of the limits of the user.
The current task will be to find the administration directory.
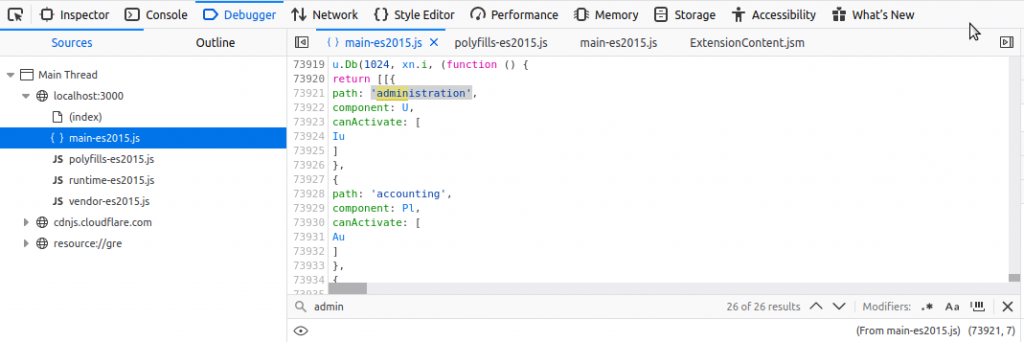
I’m reviewing the page with the word “admin” because I’m going to need to search for an administrator-related directory.
http://localhost/#/administration
If you do not log in with the admin user, we will receive the following warning.
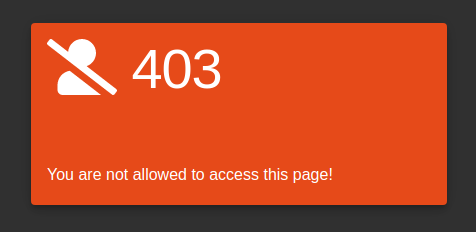
In the previous task, we were able to log in with the “administration” user through SQL Injection. Try the same method again and reach the directory.
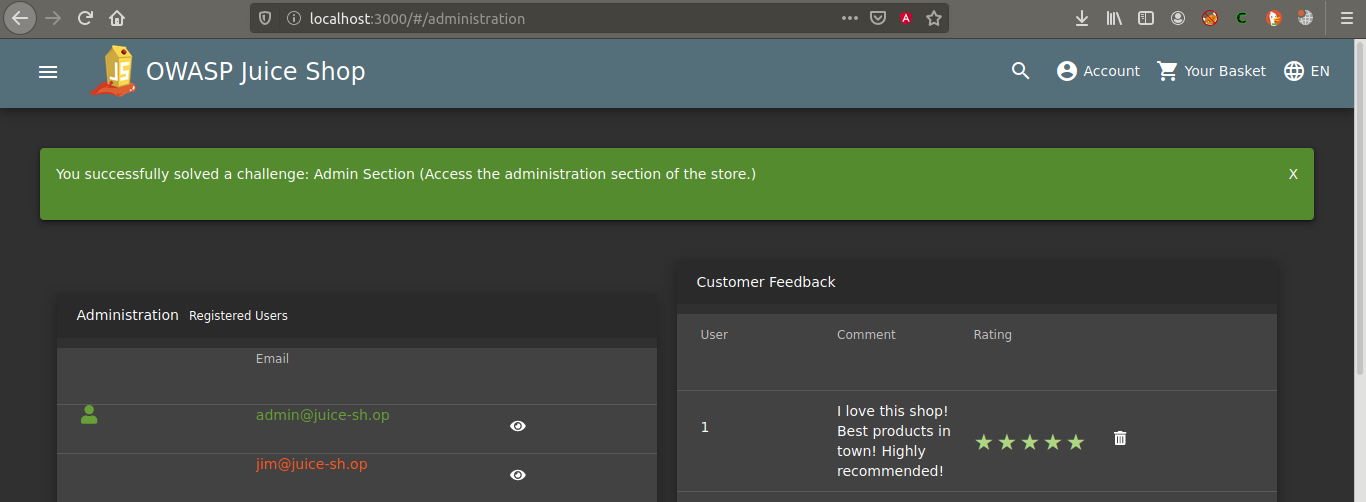
TASK – 3
Name: Classic Stored XSS
Describe: Perform an XSS attack with <script>alert(`xss`)</script> on a legacy page within the application.
Category: XSS
To summarize Stored XSS briefly, the XSS codes entered in the input are saved in the database. Then the user who enters the page is exposed to the XSS attack.
Now it’s to find an entry where we can save our XSS code. “A Legacy Page” was given as a clue. After logging in as a result of my attempts, I see different reactions in the username section on the incoming profile tab…
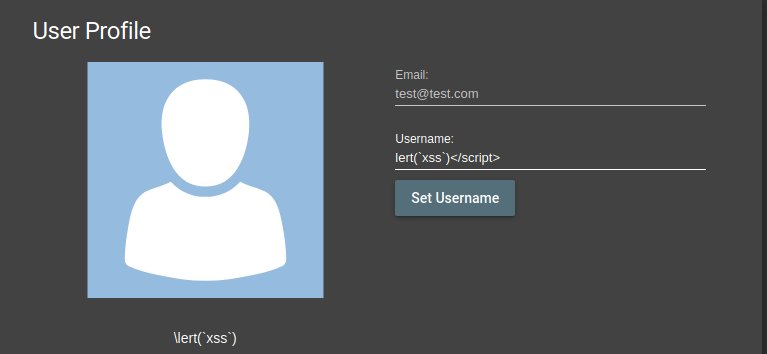
The input I enter is reflected to me as filtered on the backend. If i need to list the responses of some XSS scripts which I send;
- <script>alert(`xss`)</script> ——– > lert(`xss`)</script>
- <script>aalert(`xss`)</script> ——- > alert(`xss`)</script>
- <sssscript>alert(123)</script> ——- > lert(123)</script>
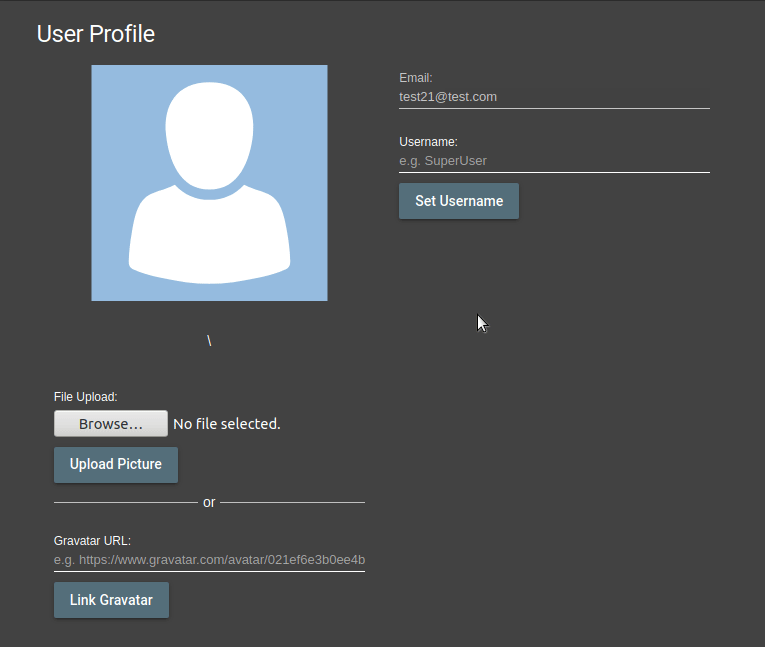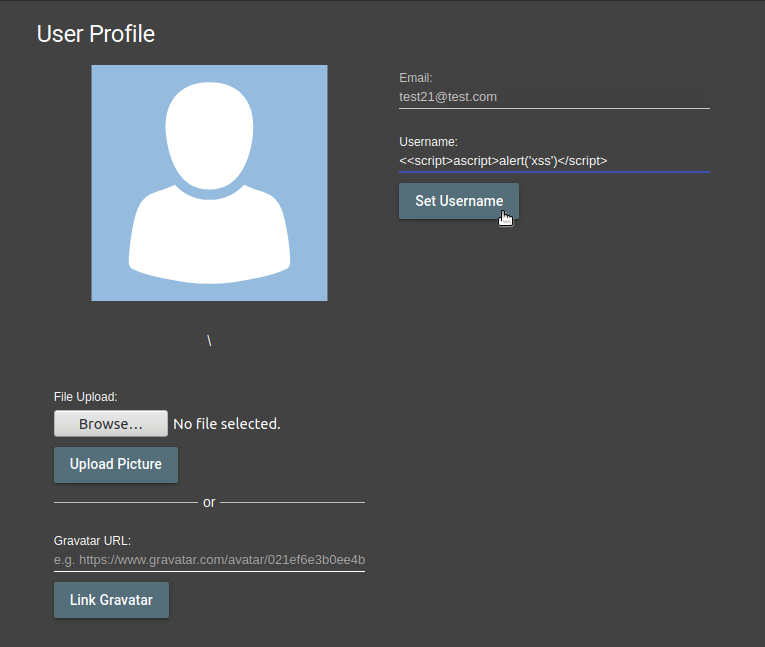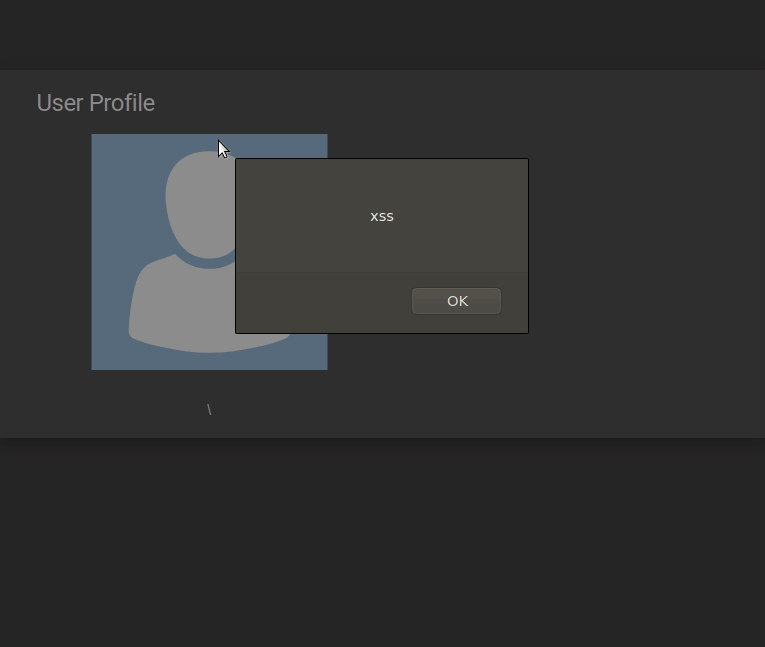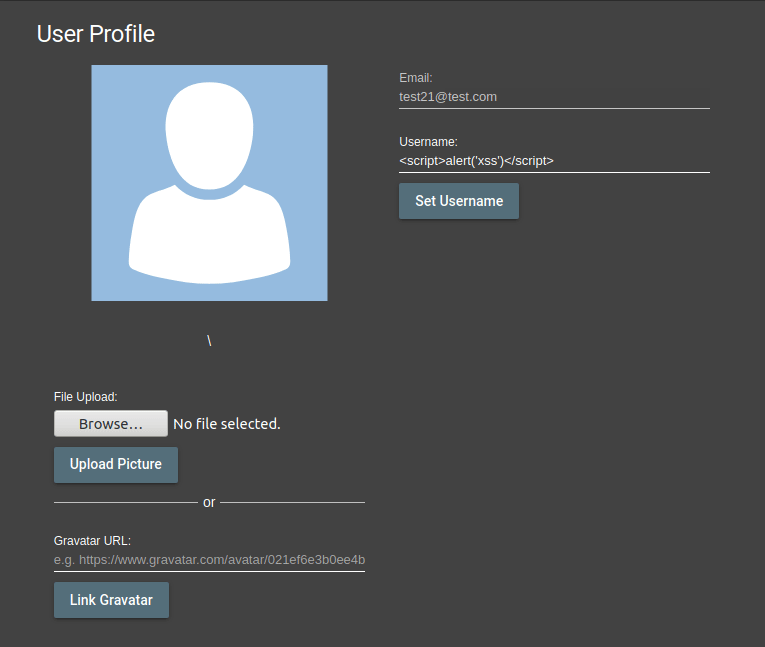
My goal is to print the value and prevent the value after it from being deleted. I was finally able to find an entry in the experiment.
<<script>ascript>alert(‘xss’)</script>
The field I mark as italic will be filtered and deleted on the server side. That’s what’s left of this script; <script>alert(‘xss’)</script>
Now when any user visits my profile or sees my username somewhere, XSS payload will be triggered…
TASK – 4
Name: Deprecated Interface
Describe: Use a deprecated B2B interface that was not properly shut down.
Category: Security Misconfiguration
Our current goal is to detect a misconfigured vulnerability in a deprecated B2B interface. The intention of removing it completely is whether the source used to be on the server and no longer existed. This means that the source will either make 404 errors or will issue 410 errors.
For example, Search engines may insist on re-scanning a page with a “404 Not Found” page not found error message, in the future to index the page and its content. However, in the “HTTP 410 Gone” error message, the search engines are given the message clear and precisely removed from this page via the server.
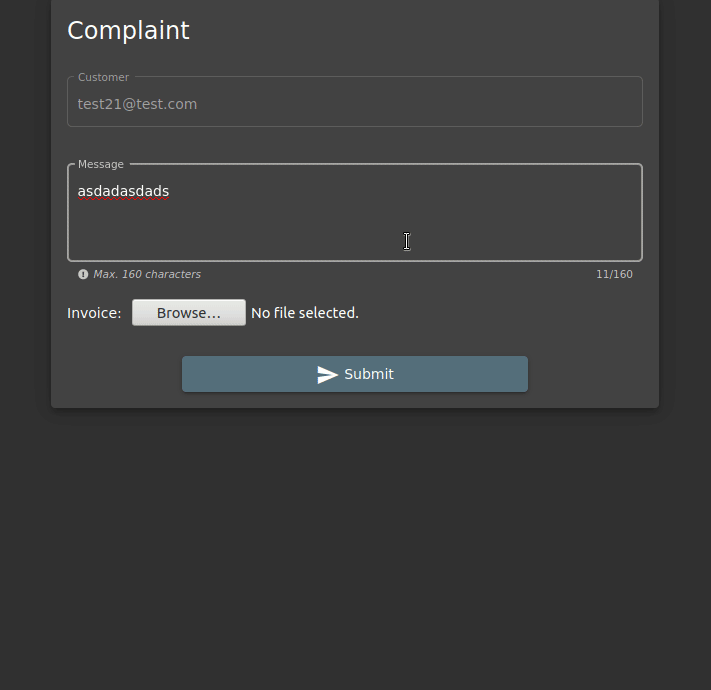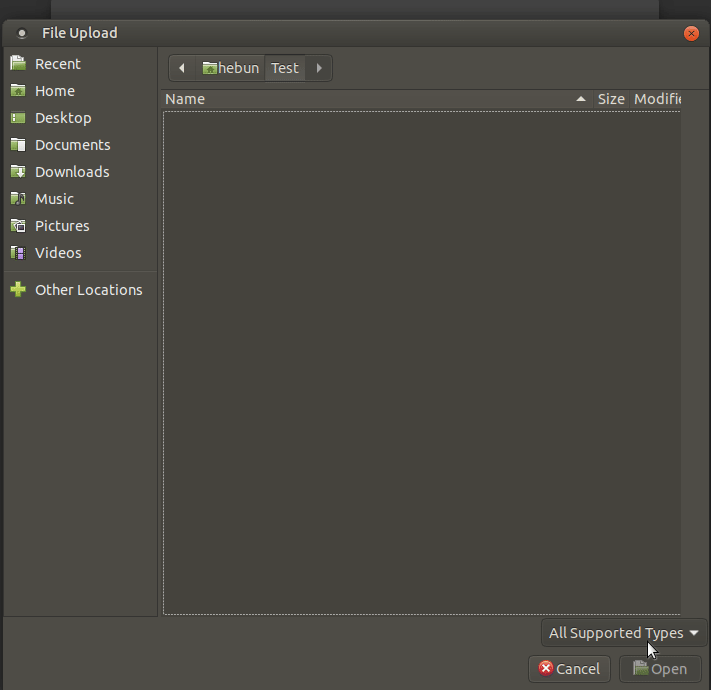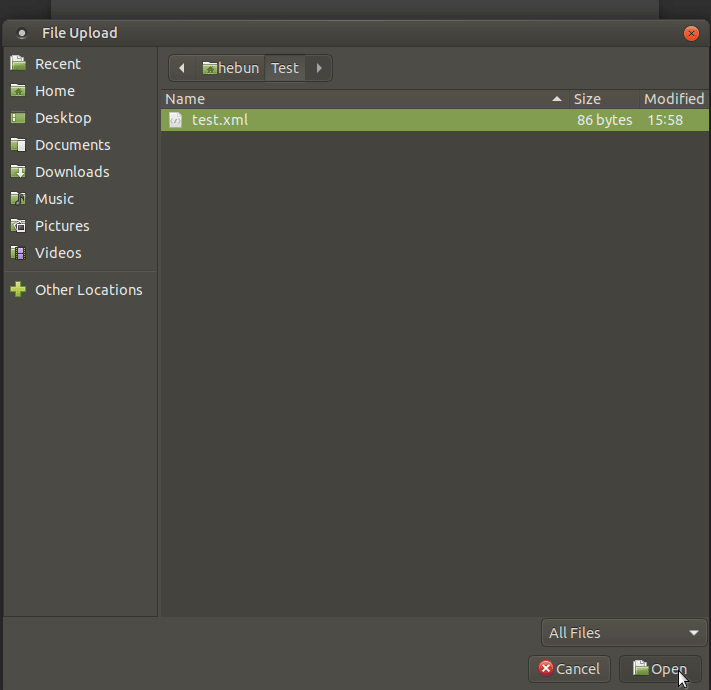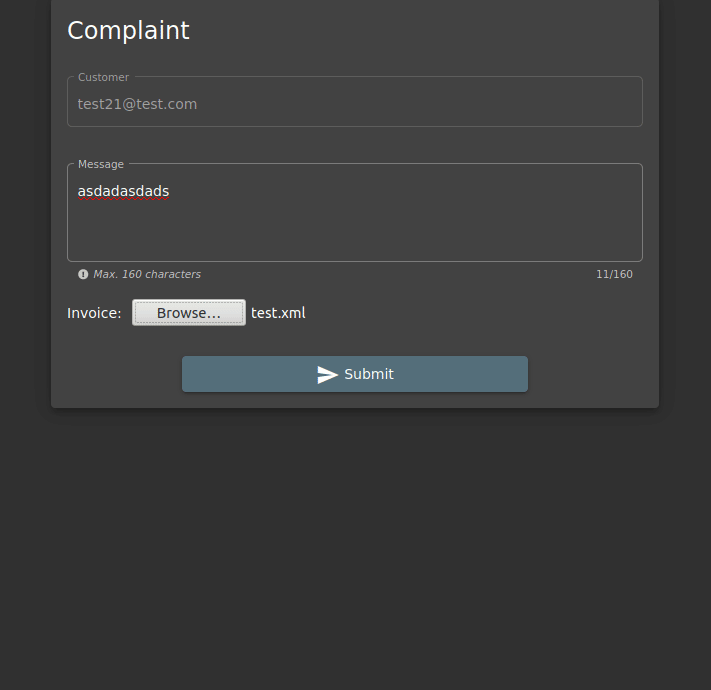
So the error that should be taken due to decommissioning must be “410”. Once you’ve logged in to the site, let’s enter the Complaint tab from the navigation bar.
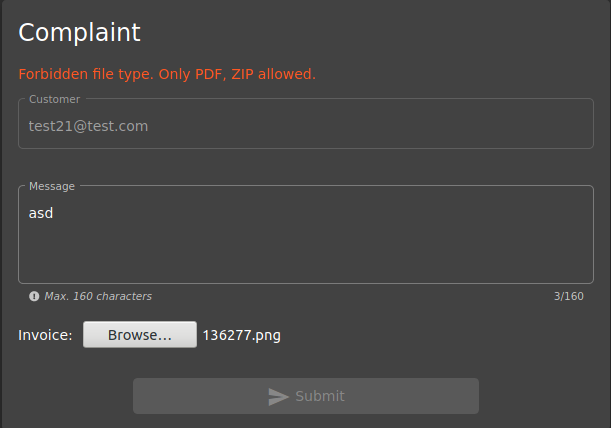
When I try to upload a PNG file, I get a warning that I can just upload a PDF and ZIP file. Let’s use Developer Tools…

Files that are accepted other than PDF and ZIP. Let’s create an XML file and check that we can upload the file.
Since the xml file we want to upload is not in the “All Supported Files” category, we should try to install it by saying All Files.
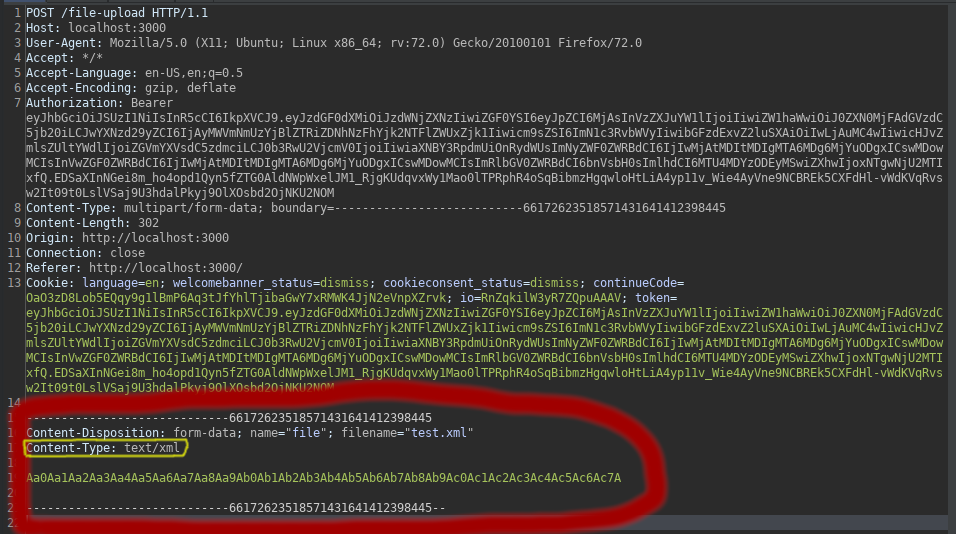
Let’s capture and examine our request through burp. We see the file type I want to send in the Content-Type header. The contents of the XML file are the following random value.
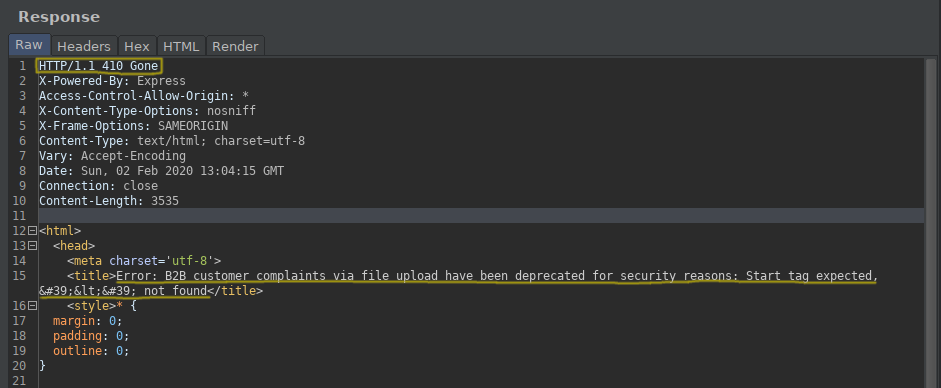
Error 410 is coming as HTTP Status Code that we check for response. When we check the following title, there’s an explanation as to why this page was removed. For security reasons…
So what could be this security vulnerability? E-Commerce sites typically use XML for data exchange. XML provides a great advantage in Busines To Busines (B2B) applications here. This is because it is text-based and easy to understand.
The XXE (XML External Entity) Injection attack can read sensitive data in the system. Even the command can be run on the system…
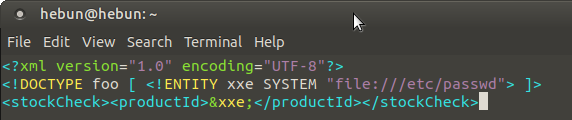
To give an example without going into detail, It defines an external entity &xxe; whose value is the contents of the /etc/passwd file and uses the entity within the productId value in the above payload.
TASK – 5
Name: Five-Star Feedback
Describe: Get rid of all 5-star customer feedback.
Category: Broken Access Control
If you remember Task-1, you know how we logged in with an “administrator” user using SQL Injection and how we find the “administrator” directory in Task-2. Now let’s delete 5 Star reviews by taking advantage of the vulnerabilities we found…

TASK – 6
Name: Login MC SafeSearch
Describe: Log in with MC SafeSearch's original user credentials without applying SQL Injection or any other bypass.
Category: Sensitive Data Exposure
The biggest reason most users are hacked is because the level of awareness is low. We’re used to passwords being predictable easy passwords. Nowadays, users offer their passwords to malicious people with a gold tray.
Sample scenario:
Let’s assume that “A” is his favorite book, “And Then There Were None”. Let’s say “A” shared the book on Twitter or Instagram. Let’s say “A” talk about book everywhere in a friend environment… In fact, let’s imagine that “A” used this book as a password on his social media accounts…
As you can see, it is offered on a gold tray… Current task MC SafeSearch is asked to login to the site without using SQL Injection.
Once we have access to the Administration directory, we are looking for a tip for this MC SafeSearch and we’re identifying the email address. Now let’s have a little social engineering experience on Google.
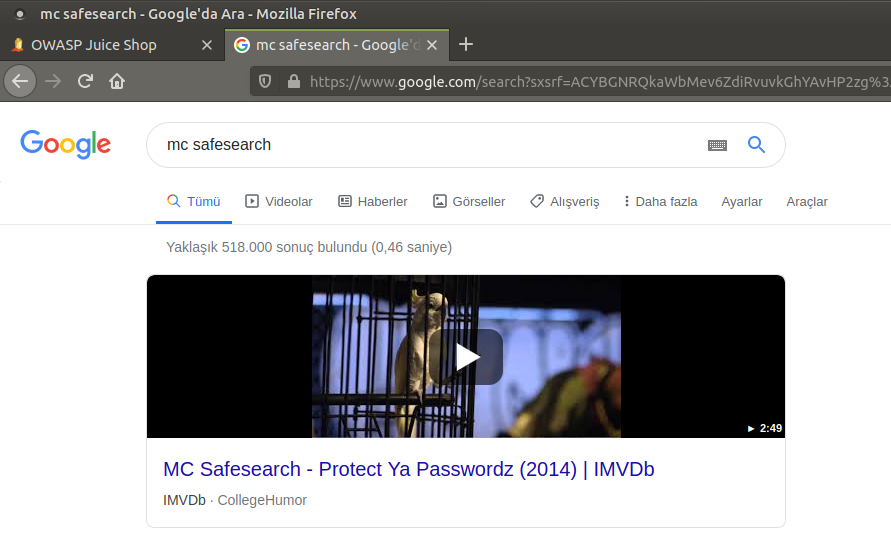
When I search “MC SafeSearch” on Google, I see a clip. I hope to find a clue in a rap song with the topic “Rapper Who Is Very Concerned With Password Security”…

In one part of the clip, MC SafeSearch sings the name of him favorite dog. “Mr. Noodles”. When I tried to log in using the knowledge “mc.safesearch@juice-sh.op:Mr. Noodles”, I was unable to succeed. Let’s continue listening to the song…
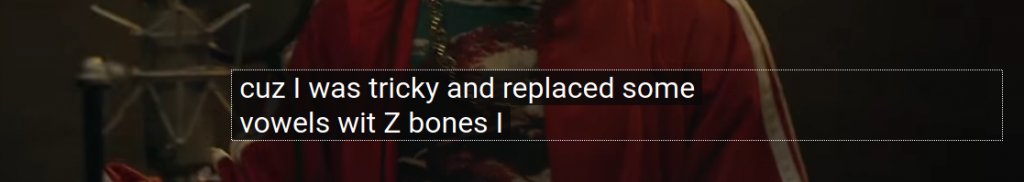
In one section, our friend claims to have made it difficult by replacing the vowels with “0.” Then let’s try the password as Mr. N00dles…
TASK – 7
Name: Password Strength
Describe: Log in with the administrator's user credentials without previously changing them or applying SQL Injection.
Category: Broken Authentication
I think we understood that the more hidden the password is in Task-6, the harder it is to find it… The current task will be the unique difficulty of the password. We are asked to log in with the Administrator user, but SQL Injection will not be used here.
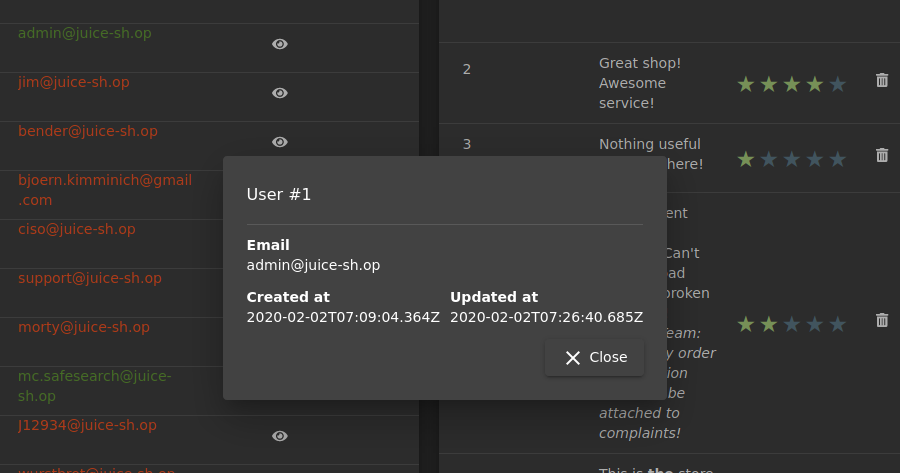
We were able to find the user’s email address in the “administrator” directory. All we have to do here is guess the password… I’m going to try brute force attack here using burpsuite’s Intruder function.
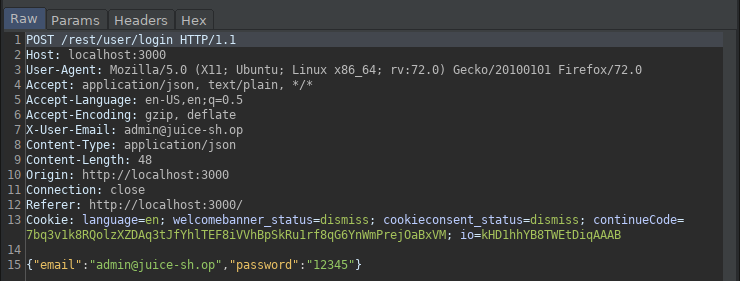
Let’s catch the request at Burp when we log in. Then let’s right-click and send it to Intruder.
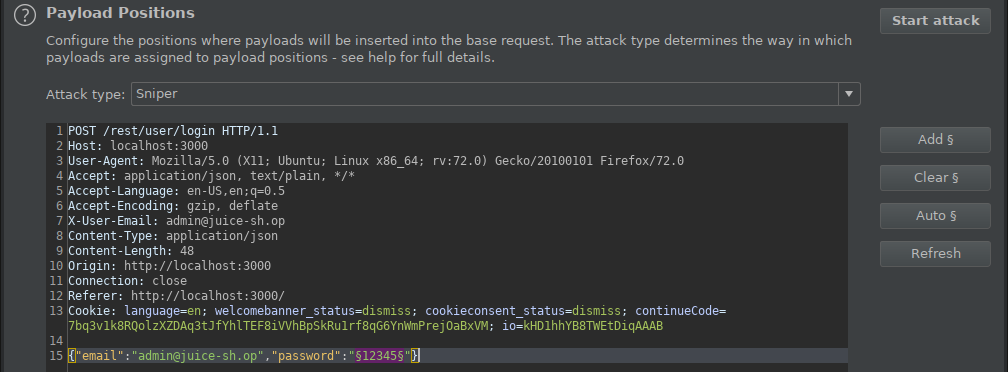
Click the clear button on the right, then select the password section (12345), and click the add button. So we’re just going to attack brute force on the password part.
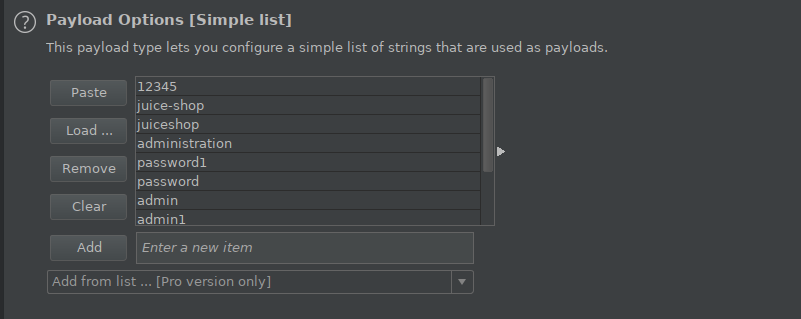
I then click on the payloads tab and add the passwords which I’ll try for Brute Force in Payload Options. After I write the password that comes to my mind, I start the attack.
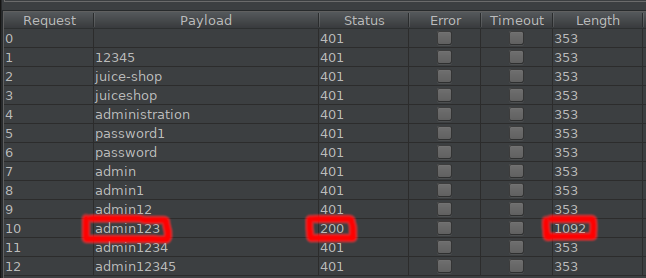
Here I find the password according to the HTTP status codes and the length of the value received in the response. “admin123” says that the password has 200 codes, so the operation is successful. Also received data is 1092 Bytes. When we try the password, we have completed our task.
TASK – 8
Name: View Basket
Describe: View another user's shopping basket.
Category: Broken Access Control
Web Storage offers 2 options for storing data as Local Storage and Session Storage. These two storage options are defined as key;value. In Local Storage has no expiration date for data, In Session Storage is deleted when the web browser is closed.
Let’s focus on our mission with information above…
Our goal will be to view the products in another user’s basket. Let’s create two test user accounts to detect this vulnerability.
- test1@test1.com
- test2@test2.com
I’m adding a product from the home to the basket for test1 user. I then open the Private Browsing and sign in with test2.
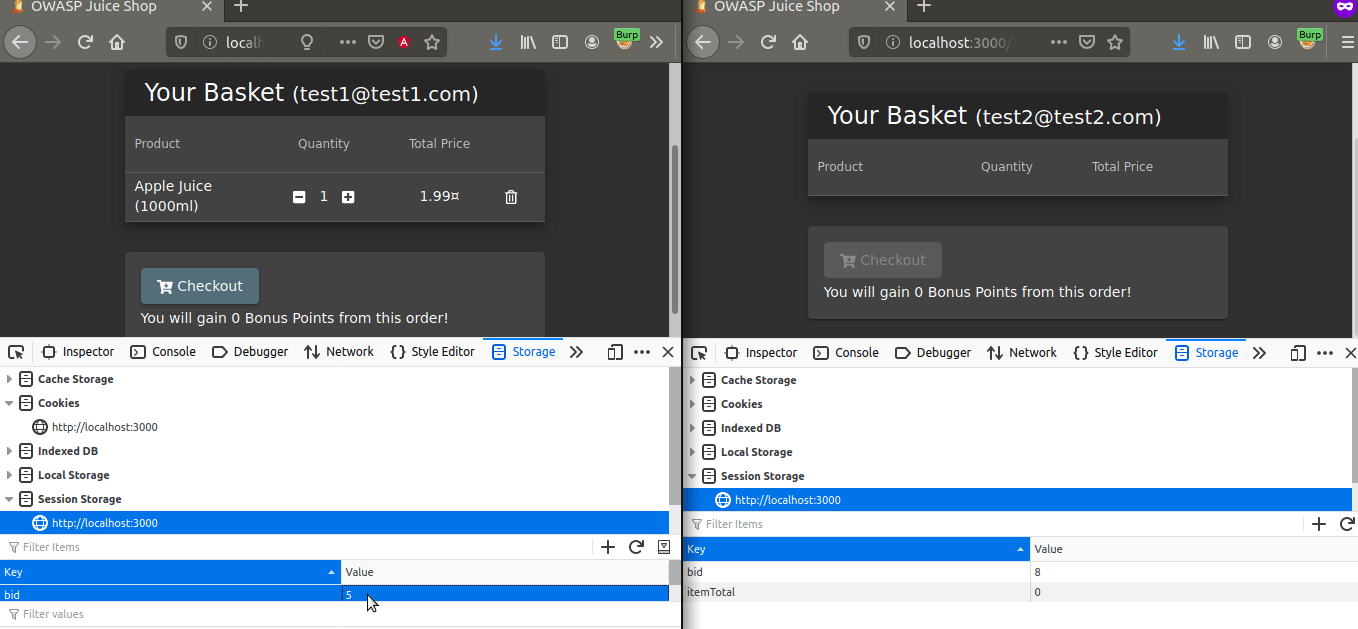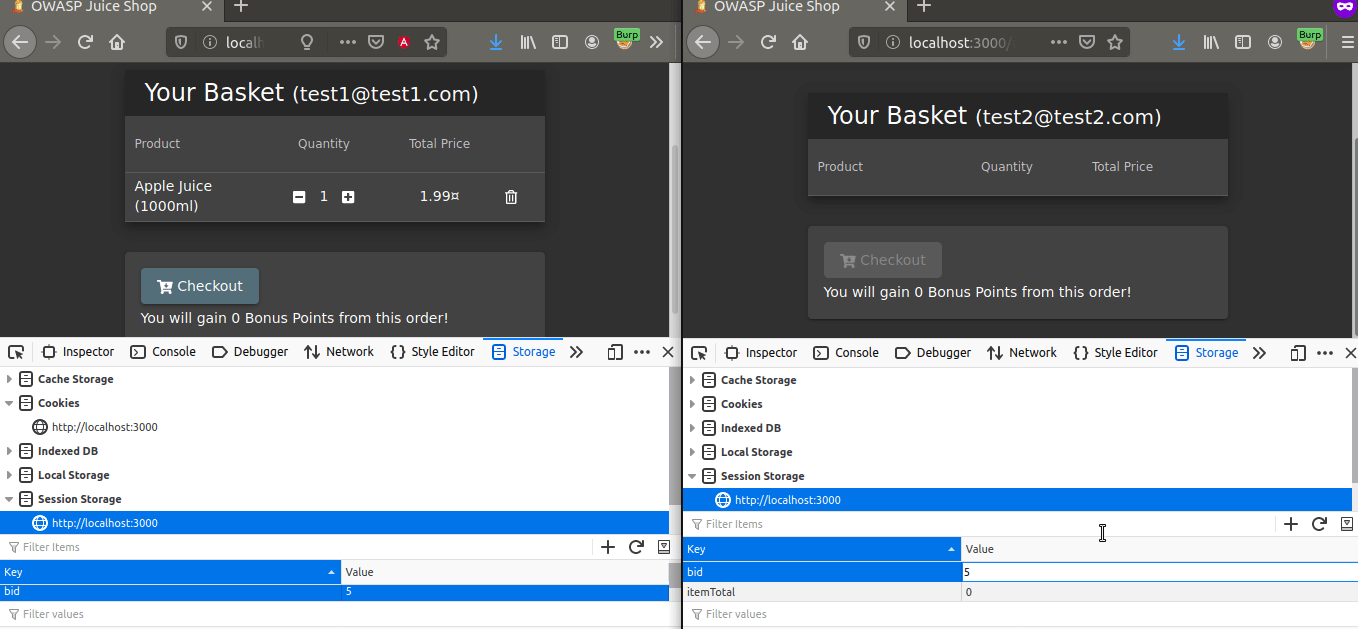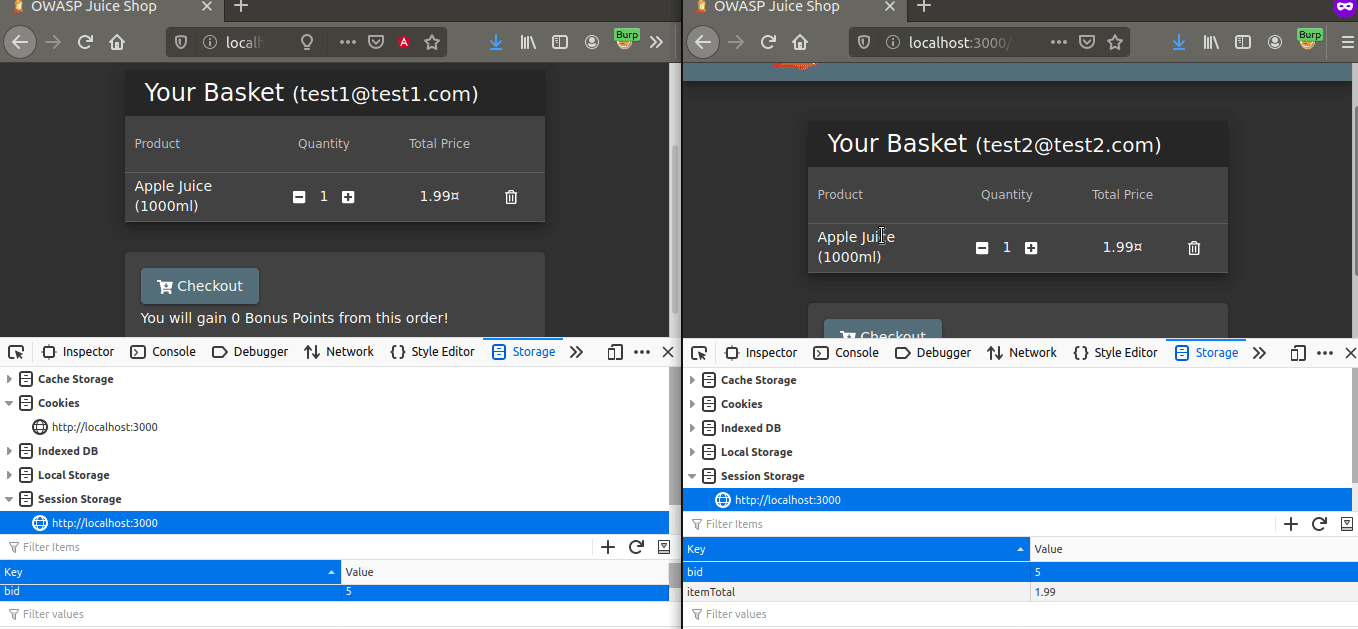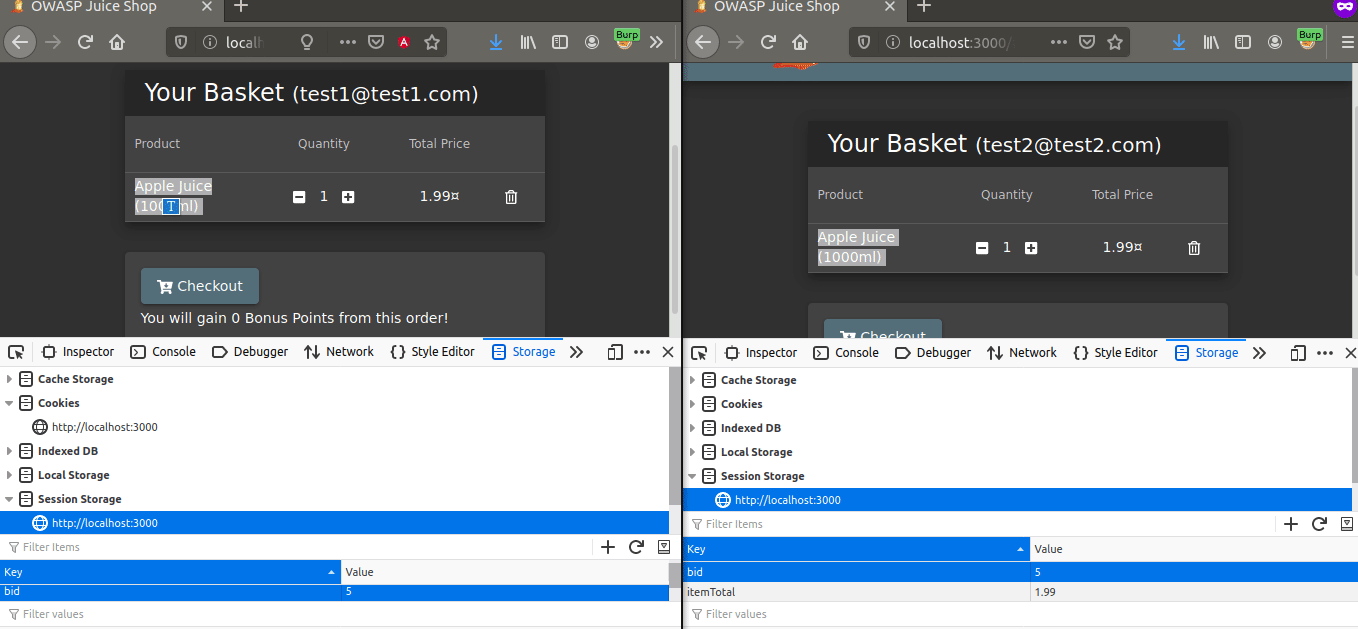
Let’s click Storage tab from Developer Tools and see what happens in Local Storage and Session Storage.
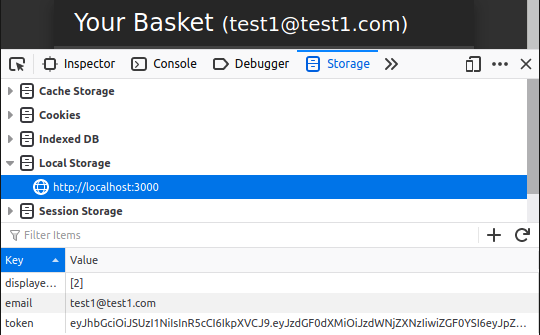
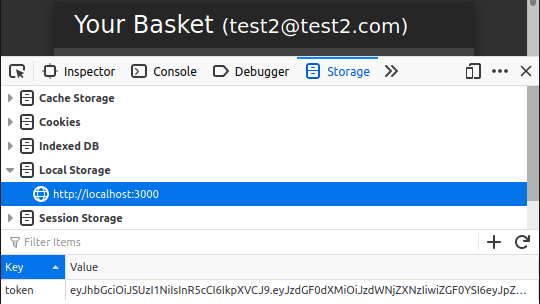
If you’ve noticed in Local Storage, some keys are not visible in test2. This is because of Pivate Browsing. You know that Private Browsing doesn’t record any data…
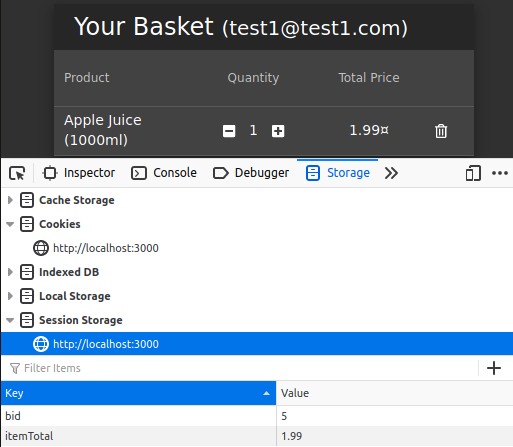
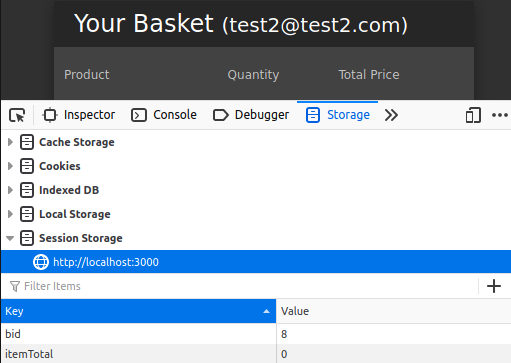
When we look at Session Storage, we see two key. These are; Basket ID and Total Price represent. Test1’s Basket ID doesn’t mean that it’ll always be 5. Because, as I mentioned at the beginning of the article, In Session Storage is deleted when the web browser is closed. So when the user uses the browser again, that Basket ID can get another value…
Let’s go back to the mission… Our goal is for the test2 user in the private browsing to view the basket of test1. Let’s copy current Basket ID of the test1 user and paste it into test2’s bid.
TASK – 9
Name: Weird Crypto
Describe: Inform the shop about an algorithm or library it should definitely not use the way it does.
Category: Cryptographic Issues
Our mission will be to report an algorithm or library that shouldn’t be used to Juice-Shop officials. Of course, we’re going to have to find out which libraries and algorithms are being used on the site.
If you remember, in the first article of the series, we detected the “ftp” directory using the dirb tool. Let’s look again at the ftp directory…
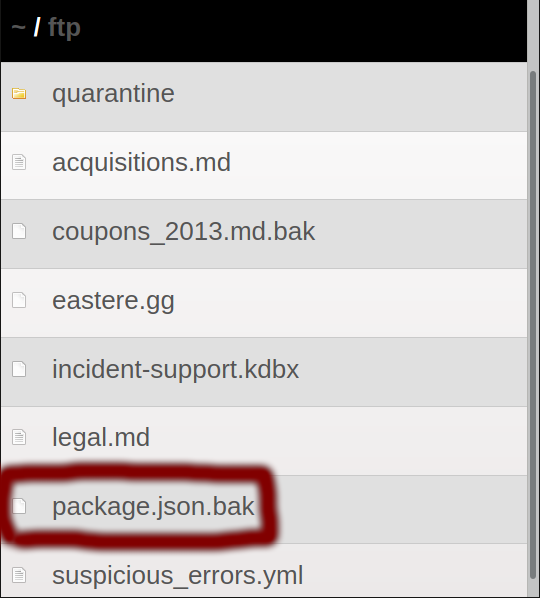
When writing the Node.js project, there is always a package.json file in the project. A local package database that contains information about packages and dependencies used in the project it is involved in. It contains objects such as name, version, description, author, script, bugs, dependencies, licence.
The part we’re going to examine will be the “dependencies” object. Dependencies object is needed to download and use packages used in the project.
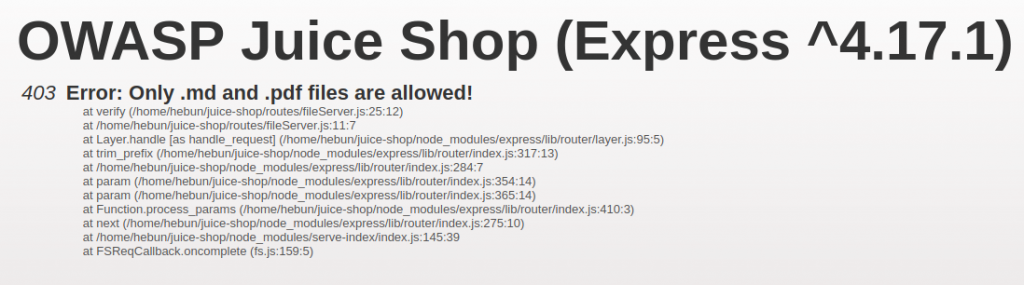
I get a 403 code when I want to access the file… The warning description stated that I could only download it as .md and .pdf.
Null Byte Injection is an exploitation technique which uses URL-encoded null byte characters (i.e. %00, or 0x00 in hex) to the user-supplied data. This injection process can alter the intended logic of the application and allow malicious adversary to get unauthorized access to the system files.
Null Byte Injection
Let me explain the above theoretical knowledge to you in an example…
For example, there is a section in the profile tab of the “A” site where we can change the profile picture. Let’s say we want to load a shell.php.png file. You guessed what this file is 🙂 We will not be able to get shell because it has the extension “.png” at the end of file… So what happens if we add Null Byte to the file extension?
“shell.php%00.png”
The value after null byte will be excluded from the string process and the file will be added under the following name;
“shell.php”
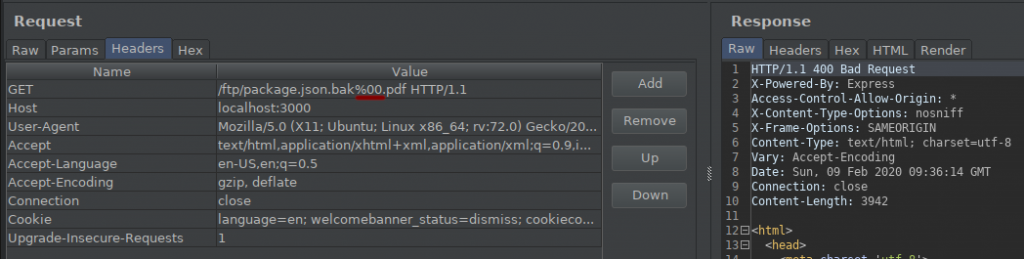
If you pay attention to the request above, I removed the pdf extension from the string concatenation process using null byte. But I got 400 Bad Request codes in response… This is because the user may be using the missing parameter, fake routing, or incorrect format in the request. A status code that specifies that the request sent briefly is incorrect. We’re probably getting this error because of the character “%.” Now let’s bypass this situation…
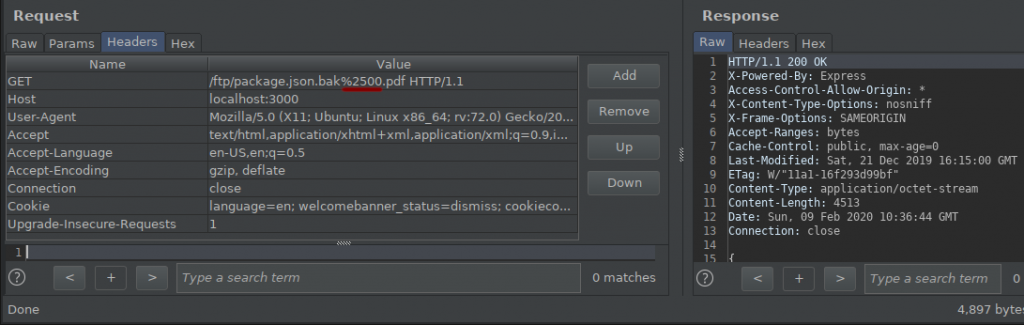
The URL Encode equivalent of “%” ASCII Character is “25%”. When I add this character;
- %2500 —– > %00
So I was able to bypass this by using url encode and after NULL bytes, I can do the “.pdf” extension dysfunctional…

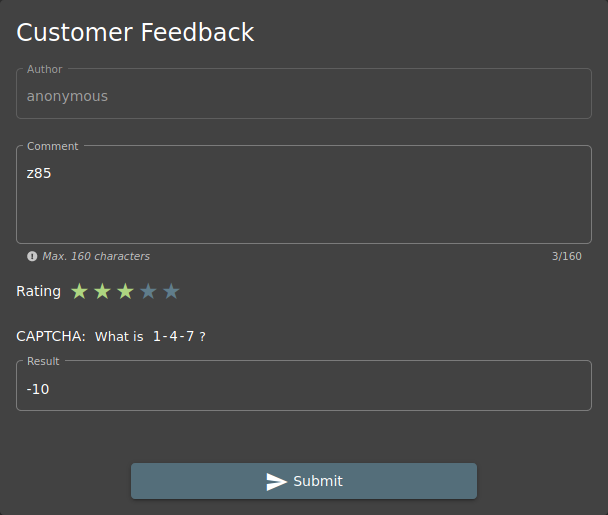
Let’s check the packages on the dependencies object in package.json.look file. Among the packages used, I only saw the ASCII85-based z85 library, and I wrote this in the comment section in Customer Feedback and completed my mission.
NOTE: There are several more types of algorithms available in this task. I could have completed the mission by writing these. But since these will be revealed in subsequent missions, I’ve gone this way and completed the mission. For your information…
It was a long article. I hope it was a sufficiently useful explanatory article. If I have any errors, please contact me and let me correct this error. See you in the next article…